
(This report, on the dubious testimony of Peter Wright, the author of Spycatcher, concerning Agent Sonia and her wireless transmissions, is a long and challenging one, and I issue my customary health warning: Do not read this if you are of a sensitive disposition, or while operating agricultural machinery. I decided to lay out every step of my reasoning, with references, as I believe that, with the delivery of the authorised History of GCHQ in a few months’ time, it is important to present a comprehensive story of the slice of wartime Soviet wireless traffic that Wright focused on in his book. The interest in Spycatcher indicates that a mass of persons are fascinated by this topic: questions about possible traitors in the midst of the Security Service do not go away. I believe the issuance of this report is especially timely, as the recent feature in the Mail on Sunday should intensify the interest in the case that Wright made against Sonia and her alleged protector, Roger Hollis. If any of my readers would prefer to work with a Word version of this bulletin, in the belief that they might want to pore over it, and annotate it, please contact me at antonypercy@aol.com. After a thorough background check by my team of ultra-sensitive, highly-trained, Moscow-based security personnel, the report will be sent to you.)
“Stella Rimington and some friends in the Security Service called Wright ‘the KGB illegal’, because, with his appearance and his lisp we could imagine that he was really a KGB officer.” (Defending The Realm, p 518)
“I want to prove that Hollis was a spy; if I can do that I will be happy.” (Peter Wright to Malcolm Turnbull, from the latter’s ‘Spycatcher Trial’, p 31)
“The time has come for there to be an openness about the secret world of so long ago … the consequences of Hollis being a spy are enormous. Not only does it mean that MI5 is probably still staffed by people with similar view to him, but it means that ASIO was established on terms with the advice of a Russian spy.” (Peter Wright in the witness-box, Sydney, December 1986)
Contents:
- Peter Wright and ‘Spycatcher’
- The Background
- Cable or Wireless?
- War and Peace
- VENONA and HASP
- Wright on HASP
- The Remaining Questions
- The Drought of 1942-44
- Why did Wright Mangle the Story so much?
- Conclusions
Peter Wright and ‘Spycatcher’
As an ex-IBMer (1969-1973), until I read Spycatcher in the late nineteen-eighties, the only ‘HASP’ I knew was the Houston Automated Spooling Priority program (about which I shall mercifully write no more). One of the major contributions to mole-hunting that Peter Wright believed he made, in his best-selling account of dodgy business within MI5, was the unveiling of a new source of electronic intelligence, namely (as he described it) ‘the wartime traffic stored by the Swedish authorities known as HASP’. By citing a previously unknown and ever since unrevealed message that purported to indicate the size of Sonia’s ‘network’ of spies in 1941, Wright’s assertion has exerted quite a considerable influence on the mythology of Soviet ‘superspy’ SONIA. If judged as credible, his testimony boosts her achievements in England even beyond what the woman claimed in her memoir, Sonya’s Report. Moreover, Wright used this discovery as a major reason for confirming his belief that Roger Hollis was the Soviet mole known as ELLI: he drew attention to this accusation in his presence in the witness-box during the Spycatcher trial, and thus the process by which he came to this conclusion is of profound significance.
Spycatcher sold over two million copies. This success was mainly due to the outcome of Her Majesty’s Government’s lawsuit against the author before publication, with Malcom Turnbull’s successful defence in the trial of 1986-87 issuing a stern blow to the forces of hypocritical secrecy. He was able to show that the British authorities had connived at, or even encouraged, the publication of Chapman Pincher’s two books, Their Trade is Treachery, and Too Secret Too Long (as well as Nigel West’s A Matter of Trust), which made nonsense of the claim that a ban on the whole of Spycatcher was necessary for security reasons. It was the obstinacy of Margaret Thatcher, abetted by poor advice, that caused the lawsuit to be pursued. The irony was that it was Wright who had fed Pincher most of his stories, and Pincher would later amplify Wright’s case against Hollis with the very influential Treachery. That is why this article is so important. Those two million-plus readers need to learn the facts about a critical part of Wright’s story.
The Background
Another significant outcome of a careful study of Wright’s claims concerning the HASP story is the uncovering of secrets about the interception and decryption of electronic traffic that the British intelligence services (MI5, MI6 and, especially, GCHQ) would rather the public remain ignorant of. The authorised histories of MI5 (Andrew) and MI6 (Jeffery) steered well clear of analysis of the mechanics of wartime electronic espionage, since these volumes were designed and controlled as organs of public relations. No discussion of Sonia, or the controversies surrounding illicit wireless in wartime Britain, can be found in their books, and Andrew (especially) points readers towards the secondary literature without any indication of how reliable it is, or how selectively it should be explored. Moreover, I regret that I am not confident that all will be revealed to us when the authorised history of GCHQ (Behind the Enigma, by Professor John Ferris) is published later this year. While a subsidiary objective of my focus on Wright is thus to provide a more rigorous analysis of the often puzzling story of the Allied effort to interpret Soviet intelligence traffic in World War II, a more thorough account will have to wait until a later bulletin.
The secondary literature almost universally shows an alarming confusion about the techniques and technology that underlay the surveillance of the traffic of foreign powers before, during, and after WWII. The largely American literature on the VENONA program (to which HASP was a critical adjunct: see below) is distressingly weak on technology, and focuses almost exclusively on the interception of traffic in the United States. Even such a well-researched and methodical work as Philip H. J. Davies’s MI6 and the Machinery of Spying contains only two short references to VENONA, guiding the reader (note 32, p 237) for ‘a (contested) British version of the story’ to Peter Wright’s Spycatcher. This seems to me a gross abdication of critical responsibility. Davies concentrates of human ‘machinery’, not technology, and delegates coverage of problematic matters to a source he instantly characterizes as dubious. It would appear, therefore, that, even though Wright’s story does not derive from any published archive, his controversial memoir has become the default – but flawed – authority. Yet he was a minor officer in the grand scheme of things, and an elderly man with a grudge and a failing memory when his book was composed.
It is certainly difficult to obtain reliable confirmation of the essence of HASP from other academic, or pseudo-academic, sources. One might, for example, have expected to learn about it in Richard J. Aldrich’s 2010 work, GCHQ, yet, while providing a comprehensive chapter on HASP’s cousin VENONA, the author does not mention the term. The only other analyst who appears to have written explicitly about HASP without simply echoing Wright’s account is Nigel West, in his 2009 book Venona. West has overall provided a competent guidebook to the initial breakthroughs on decryption, and an excellent coverage of the content of VENONA traffic, with emphasis on the London-Moscow communications, although it would benefit from a revision to consider the relevance of such sources as the Vassiliev Notebooks (see https://digitalarchive.wilsoncenter.org/collection/86/vassiliev-notebooks). Venona is a highly readable summary for the curious student of intelligence, but West’s coverage of the mechanics of VENONA is spotty and inconsistent. Moreover, his representation of the HASP traffic is so different from that of Wright that I believe the topic merits greater scrutiny, and it is my goal here to provide that level of inspection, and assess the validity of what Wright claimed. This is uncharted and complex territory, however, and the landscape is strewn with pitfalls.
VENONA was one of the major successes of British-American co-operation on intelligence matters after WWII. Owing to a procedural mistake in 1943, a large number of GRU (military and naval intelligence) and NKVD/KGB (* state security) messages exchanged between Moscow and outlying stations in foreign embassies employed a defective technique for enciphering highly confidential messages – the re-use of so-called ‘one-time pads’. Intelligence agencies have regarded one-time pads as the most watertight way of preventing enemy decryption of messages, and they were adopted by the Soviet Union in the 1930s. (Many readers will be familiar with the concept if they have read Leo Marks’s Between Silk and Cyanide.) Alert cryptanalysts in the National Security Agency (NSA), inspecting messages in 1946, noticed unusual patterns, and in 1948 were joined by their British counterparts from GCHQ in exploring the phenomenon. By applying painstaking techniques to detect repeated sequences, they were able to initiate a project that gradually disclosed several networks of spies in the USA, Canada, Britain and Australia, leading to the successful prosecution of such as Julius Rosenberg, Klaus Fuchs, and Alan Nunn May, and the identification of Donald Maclean. VENONA was not formally revealed to the public until 1995.
Yet exactly what this ‘re-use’ entailed, and where and when it took place, and to which cryptological tools it applied, remains one of the most vexing puzzles in the VENONA story. It is as if the practitioners, when explaining their successes to the lay historians who carried their accounts to the world, wished to keep the process and sequence of events to themselves, as a defensive measure to protect their secrets, and maybe, even, to exaggerate what they were able to accomplish. A deep integrative history is sorely needed.
[* The naming of the Soviet Security Organization changed frequently. In 1934, the OGPU was transformed into the NKVD, which for a few months in 1941 became the NKGB, before reverting to NKVD until April 1943. In March 1946, it became the MGB, but foreign intelligence was transferred to the Committee for Information (KI) from October 1947 to November 1951. In March 1953, on Stalin’s death, the unit was combined with the MVD, out of which the KGB emerged, after Beria’s execution, in March 1954. Source: Christopher Andrew. I sometimes use ‘KGB’ in this article to refer to the permanent body, as do many authors.]
Cable or Wireless?
One conundrum in the analysis of VENONA and HASP has endured: no author on the subject is precise about where and when VENONA (or HASP) was the result of intercepting cable traffic, and where and when it involved wireless traffic. This distinction is important when one considers the challenges facing the counter-espionage organisations of the nations trying to protect themselves. The term ‘cable’ is frequently used as a generic term for ‘telegram’, reflecting its historical background, but telegrams sent by wireless should definitely not be called ‘cables’. Christopher Andrew, in Defending the Realm, makes a useful distinction, but his account is incomplete and thus overall unsatisfying. He contrasts (on page 376) the regulations pertaining in the UK, where ‘even before the Soviet entry into the war, the Foreign Office had agreed that the Soviet embassy in London could communicate with Moscow by radio on set frequencies’, and adds that a project was soon underway to intercept these messages. On the other hand, no corresponding agreement existed in the USA, where, instead, ‘Soviet messages were written out for transmission by cable companies, which, in accordance with wartime censorship laws, supplied copies to the US authorities.’
This statement is probably an echo of what appears in the staff (but not ‘official’) story of VENONA, issued by the NSA/CIA in 1966 (VENONA: Soviet Espionage and the American Response, edited by Robert Louis Benson and Michael Warner). In the Preface (p xii) appear the following sentences: “Although Soviet intelligence services had clandestine radio transmitters in diplomatic missions located in several American cities, these apparently were to be used only in emergencies. In consequence, KGB and GRU stations cabled their important messages over commercial telegraph lines and sent bulky reports and documents – including most of the information acquired by agents – in diplomatic pouches.” This statement moves us closer to the truth, but in my opinion still misrepresents the essence of the Soviet strategy concerning clandestine systems, and does not explain whether these secret channels were intercepted at all.
Confusion abounds. For example, in the very first sentence of Venona, Nigel West writes of the project to intercept Japanese traffic in October 1942 as follows: “Cable 906 purported to be a routine circular in seven parts and, as it had come off the wireless circuit linking Tokyo to Berlin and Helsinki, it underwent the usual Allied scrutiny to see if it betrayed any information of strategic significance.” Cables cannot ‘come off’ (whatever that means) ‘wireless circuits’, and it is inaccurate to describe temporary wireless paths as ‘circuits’, since wireless transmission is by definition unconnected. It makes sense to refer to a ‘circuit’ linking ‘Tokyo to Berlin and Helsinki’ only in terms of a conceptual agreement about callsigns, frequencies, and schedules between intelligence services and outposts. As another example, the heading for the NSA’s official packaging of the London to Moscow traffic (at https://www.wilsoncenter.org/sites/default/files/media/documents/article/Venona-London-GRU.pdf ) is titled ‘London GRU – Moscow Center Cables: Cables Decrypted by the National Security Administration’s Venona Project’, a regrettable misrepresentation of reality. The messages were sent by wireless.
The misconception is aggrandized by Peter Wright himself. In Spycatcher, the author, the self-professed expert in these matters, writes (p 182): “Whereas the Americans had all the Soviet radio traffic passing to and from the USA during and after the war, in Britain Churchill ordered all anti-Soviet intelligence work to cease during the wartime alliance, and GCHQ did not begin taking the traffic again until the very end of the war.” Sadly, every clause of this woeful sentence contains at least one blatant error, which casts serious doubt on his reliability on other matters. Specifically:
- The Soviet VENONA traffic to and from the USA was almost exclusively commercial cable traffic.
- ‘Had all the Soviet radio traffic’ is meaningless. Did the Americans intercept it all? Most certainly not. As other experts have pointed out, wireless traffic was banned (officially) during the war. The Soviets used wireless as an emergency back-up system, but also as a channel for clandestine espionage traffic.
- No one can point to the minute where Churchill ordered all interception, let alone all intelligence work, to cease. Hinsley’s famous footnote [see below] speaks only of ‘decryption and decoding’, not interception, and does not constitute an authoritative record. (Professor Glees reports conversations with Hinsley on this point in his book The Secrets of the Service: what Glees was told, namely that the Y Board may have issued such an order, now appears to be confirmed by the in-house history of the NSA.) We know that interception of signals continued, if erratically, throughout the war, and that Alastair Denniston, previously head of GC&CS, started his new project on Soviet traffic in late 1942.
- GCHQ did not come into existence until 1946. Before that the institution was known as GC&CS (Government Code & Cypher School). During the war, however, RSS was responsible for ‘taking the traffic’, and never reported to GC&CS. We know from RSS files that it monitored Soviet traffic, and that the ISCOT project started picking up Comintern messages in 1943.
Within this fog of misrepresentation a very important distinction remains. A cable is a wire, with the important corollary that those agencies that control the input to the physical cable may have special authority (or power) to intercept and store the traffic that is passed to them. Such transmissions can also be detected clandestinely by specialized sensory equipment, which would have to be laid close to the cable. Thus cables are a direct, bounded, targeted medium and not universally detectable. (Today’s fibre optic cables, which GCHQ and the NSA tap, follow largely the same oceanic paths used by the cables laid at the end of the nineteenth century.) Wireless traffic is looser: it is transmitted over the ether. It may be picked up by local groundwaves, or, remotely, by any receiving device that is geographically well-positioned to receive shortwave transmissions, allowing for the vagaries of atmospheric conditions, and frequencies used. Yet, while the atmosphere is lawless, the source of the transmission is frequently concealed, and the activity unpredictable. Wireless transmission presents a completely different set of security challenges.
P. S. I am grateful to Ian W. who, on the day this report was published, informed me that ‘cables’ might be transmitted for part of their journey over ‘wireless’ links – something I had suspected, but had not been able to verify. Ian also mentioned that, half a century ago, it was common for wireless contacts to be referred to as ‘circuits’.
War and Peace
Earlier in the century, circumstances – and improvements in technology – had encouraged the use of wireless as a medium for confidential traffic. Private or nationally-owned cable facilities had been shown to be liable to attack and destruction. Such sabotage happened when the British cut Germany’s nationally-owned transatlantic cables in 1914, an event that forced German diplomatic traffic to be routed through ‘neutral’ third parties. Britain used its sway to intercept German traffic, and with cryptological skills abetted by the provision of codebooks supplied by the Russians, started deciphering German messages. In February 1917, the British deciphered the Zimmermann Telegram, which had encouraged Mexico to join forces against the United States. When Zimmermann admitted the truth behind the cable telegram, public disgust brought the USA into the war.
Such an exposure encouraged experimentation with a rapidly developing wireless technology. (In Spycatcher, Peter Wright himself explained how, after World War I, his father assisted Marconi in convincing the British government that the beaming of short-wave wireless signals would be more effective than deploying long-wave technology as a means of linking the Empire.) In turn, as practices and understanding matured, that led to the important adoption of water-tight encryption mechanisms. Correspondingly, in the next two decades of peace, host governments tried to monitor such processes that originated on their home territory, by attempting to pick up open transmissions from the air, to set about decrypting them, and thus identifying possible hostile threats. The British project known as MASK, which detected Comintern traffic in London in the mid-thirties, was an example of such.
The advent of war, however, made a more spirited approach to trapping and prosecuting illicit wireless transmissions much more urgent. For example, at the outset of World War II, the British were fearful of the possibility of swarms of enemy wireless operators in their midst. They were initially not so scared about routine intelligence-gathering as they were about the (imaginary) menace of such spies using wireless to guide German bombers to their targets. The government also wanted to control the dissemination overseas of secret intelligence by conventional agencies. It made demands to foreign embassies and legations about being informed of wireless frequencies, and even call-signs, before giving approval for their use. Since a tacit understanding about reciprocal needs existed, governments often turned a blind eye to some technical breaches (such as the British with the Soviets, and the Swiss with the British). To monitor abuse of the airwaves, interception services then had to deploy enhanced wireless detection mechanisms to collect such clandestine messages, and maybe direction-finding/location-finding systems and vehicles to verify the source of such messages (as happened with the Soviet Embassy in London in 1942.) The elimination of any possibly overlooked German wireless agents was critical for the success of the Double-Cross system.
The UK government thus permitted the use of wireless transmitters on embassy premises only for Allies, while allowing, as a special case, the Polish and Czechoslovak governments-in-exile to have their own independent wireless stations, the Czech station in Woldingham, Surrey playing a very significant role. In the UK, all represented governments (including those in exile) clearly had a preference for using wireless rather than cable, in the belief that the traffic might not be picked up at all, and thus be more secure. The Soviet Union was in a unique position, as it was officially neither ally nor enemy from September 1939 until June 1941, but was hardly neutral, as it had, in that period been in a pact with Nazi Germany, and had aided the latter’s war effort against Great Britain. In those circumstances, it was supposed to use its wireless apparatus in the Embassy for diplomatic traffic only, and was instructed to inform His Majesty’s Government of frequencies and callsigns being used.
Thus, when any embassy or legation in World War II wanted to send a ‘telegram’, it still maintained some level of choice. First, it had to deal with the local government, consider the regulations, and assess how strictly the rules were going to be enforced. Indeed, many such messages were enciphered, but still sent over private circuits. Copies were frequently taken by the local authorities, especially by those who (as with the USA) forbad the use of clandestine wireless by foreign governments. Indeed (as Romerstein and Breindel remind us in The Venona Secrets), in 1943 the US Federal Communications Commission detected illicit radio signals coming from the Soviet consulates in New York and San Francisco, and confiscated the apparatus. Consequently, the NKVD and GRU in the USA had to rely almost exclusively on commercial telegraph agencies to send their messages to Moscow. Likewise, all confidential traffic beyond the diplomatic bag that was sent back to Moscow by the embassy in Canberra, Australia (a vital VENONA source), was officially transmitted by commercial cable companies.
Romerstein’s and Breindel’s account corresponds in general with what NSA officers have written. Their statement is an echo of what appears in Benson’s and Warner’s history mentioned above. In that work’s Preface (p xii) appear the following sentences: “Although Soviet intelligence services had clandestine radio transmitters in diplomatic missions located in several American cities, these apparently were to be used only in emergencies. In consequence, KGB and GRU stations cabled their important messages over commercial telegraph lines and sent bulky reports and documents – including most of the information acquired by agents – in diplomatic pouches.”
Yet the FBI offers an intriguing twist to this story. In the archive of that institution (‘The Vault’) can be found some provocative assertions. An undated memorandum outlining considerations in using VENONA information in prosecutions (p 63) declares that ‘these Soviet messages are made up of telegrams and cables and radio messages sent between Soviet intelligence operators in the United States and Moscow.” While that is an implausible triad (cables and radio messages are both ‘telegrams’), it suggests a more complicated situation. And, on page 72, the writer measures, with some timidity, some political considerations, indicating that the Soviet Union might react in a hostile fashion to the news that the USA had been spying on its wartime ally, thus not acting ‘in good faith’. He writes: “ . . . while no written record has been located in Bureau files to verify this it has been stated by NSA officials that during the war Soviet diplomats in the U.S. were granted permission to use Army radio facilities at the Pentagon to send messages to Moscow. It has been stated that President Roosevelt granted this permission and accompanied it with the promise to the Soviets that their messages would not be intercepted or interfered with by U.S. authorities.”
One can imagine the frequently naïve Roosevelt making an offer like this, but it is difficult to imagine that the wary Russians would take such an offer at face value, and have their cypher-clerks trek over to the Pentagon to send their material in the knowledge that it would probably be intercepted. Moreover, not all their traffic derived from Washington: New York and San Francisco were busy outlets. The item is undated, and apparently unconfirmed, and thus needs to be recorded as a footnote of questionable significance.
On the other hand, what is certain is that the Soviet Embassy in London breached the rules, even before Barbarossa, first of all by sending not just diplomatic traffic but also military and intelligence reports to Moscow on the acknowledged channels. Yet Soviet Military Intelligence (the GRU), which was for a while the only functioning intelligence unit in the Soviet Embassy, as the NKVD officers had reputedly been recalled for almost all of 1940, went far beyond what was permitted in order to deceive surveillance mechanisms. I refer to a VENONA message of July 17, 1940, from London to Moscow, which is titled ‘Setting up an illicit radio in the Soviet Embassy’. It unambiguously refers to apparatus sent over in the diplomatic bag, but without clear instructions, and requests more guidance on setting up the antenna. The GRU in London was trying to establish an alternative mechanism for transmission without informing its hosts, and, when the GRU rather absurdly suddenly were about to run out of one-time pads in August/September 1940, messages at that time specify that the ‘emergency system’ should be used. The emergency system was planned not just as a back-up procedure using a book-directed system for creating random keys (in place of the printed one-time pads), but as the deployment of an alternative wireless transmitter/receiver apparatus. (I analyse this phenomenon in more detail at the end of this report.)
To summarize, in the context of World War II: the pressures on combatants to prevent unauthorised intelligence from leaving the nation were intense. The distinction between the media was very important, as cables were finite, self-contained, and asynchronous, and could easily be collected by the host country. Wireless messages, on the other hand, were open, unconstrained, and always somewhat speculative, but required a sophisticated infrastructure just to be intercepted. Synchronicity was the goal with wireless, but was not always achieved: your target might not pick up your message and acknowledge it, or might receive it only partially. On the other hand, an unintended bystander might intercept it. Moreover, to circumvent the efforts of the authorities, units wanting to send intelligence back to their controllers would sometimes set up alternative wireless systems in secret, of which the local government had not been notified. I do not believe any analyst of VENONA has explained in detail how the respective traffic was transmitted or collected in each country, i.e. by cable, by authorised wireless, or by unauthorised wireless. Certainly, the experience – and opportunity – differed greatly for the British and American authorities.
VENONA & HASP
This confusion appears to have leaked into the VENONA-HASP muddle. In order to put the HASP phenomenon into the context of VENONA, I shall soon turn to the texts of Peter Wright, the primary source about HASP, and add detailed commentary on each passage. One of the difficult concepts to bear in mind with VERONA and HASP is that decryption (with the exception of the Australian intercepts) did not happen in real time. We are thus dealing with a process that attempted to decrypt messages that may have been transmitted two or three decades earlier, which were intercepted and stored at the time, but represent only a small percentage of the total messages that could have been theoretically available. Thus discontinuities and gaps are par for the course. Moreover, it is important to understand that the Soviets did not realise for several years that their systems had been exposed, and consequently did not rush to fix the problem. The fact of the breakthrough was revealed to the Soviets by the spies William Weisband and Kim Philby in 1949. Only then did the Soviets change their procedures, but they could do nothing about the historical traffic of 1940-48.
VENONA itself is a murky project filled with anomalies and unanswered questions, beyond the scope of analysis in this article. The set of facts that need to be borne in mind when considering HASP are the following:
- The key years of 1940 (when John Tiltman received a GRU code-book from the Finns); 1945 (when the damaged Soviet codebook gained at Petsamo was acquired by the USA, and when the GRU cypher-clerk Igor Gouzenko defected in Canada); 1946 (when Meredith Gardner made the first major VENONA decryption); 1949 (when ex-Comintern wireless operator Alexander Foote revealed GRU techniques in Handbook for Spies); 1954 (when Vladimir and Evdokia Petrov, Soviet cypher experts who had worked in Stockholm, defected in Australia); and 1959 (when the Swedes handed over HASP, the result of their decryption successes, to GCHQ and NSA).
- The GRU developed an auxiliary clandestine system to maintain secrecy. This consisted of a) an alternative method of using a secure one-time pad exploiting a reference book known to both parties (which could be used on the regular channel), and b) a separate wireless receiver-transmitter and protocols, not to be announced to the domestic authorities.
- In the USA and in Australia, the Soviet units used commercial cable channels almost exclusively. In Britain, all traffic was sent by wireless.
Wright on HASP
In 1987, Peter Wright (with the assistance of the journalist Paul Greengrass) published his best-selling work Spycatcher, an account of the efforts by the so-called ‘FLUENCY’ committee to identify a suspected mole in the senior ranks of MI5. Wright, who had been ‘chief technical officer’ within the service, was appointed chairman of the committee when it was set up in 1964. Because of the way the programme had unmasked figures such as Fuchs and Maclean, the disclosures from the VENONA project were viewed as possibly important providers of further breakthroughs. Yet successes with VENONA traffic had been slowing down in the early 1950s, and Wright stated that the project had come to a halt in 1954. A few years later a fresh injection gave the project new life. I do not intend to discuss the broader issues explored in Spycatcher: my focus is on a strict analysis of the passages where Wright writes about HASP.
Pp 185-187 [i] “In 1959, a new discovery was made which resuscitated VENONA again. GCHQ discovered that the Swedish Signals Intelligence Service had taken and stored a considerable amount of new wartime traffic, including some GRU radio messages sent to and from London during the early years of the war. “
Wright appears confused from the outset. He explicitly states that this traffic included messages that could be classified as ‘GRU’ and ‘radio’. But if this traffic had been stored, but not decrypted, how did the Swedish Service, or the receiving agency, GCHQ, know they were GRU exchanges until they were decrypted? Moreover, Wright states that these were radio messages sent ‘to and from London’. Does that mean between London and Stockholm or between London and Moscow? The suggestion could conceivably be the latter, as Stockholm would have been geographically well-situated to pick up messages targeted at Moscow, and there would be little reason for the GRU station in London to communicate with its Swedish counterpart (although a few such messages do exist in the archive). Why the Swedes would be interested, however, in intercepting and storing traffic that did not concern them directly is a puzzle in its own way. As an added complication, Fred. B. Wrixon, in his Codes, Ciphers & Other Cryptic & Clandestine Communications, states that the Swedes ‘had intercepted some GRU radio exchanges between agents [sic: my italics] in Great Britain and their headquarters in the Soviet Union’, (p 118), and that GCHQ gave the name HASP to the project to decipher them. Wrixon’s source is not stated. How Wrixon derived this information is not clear, but it eerily echoes one of Wright’s more outlandish caprices.
Did Wright mislead his readers, whether intentionally or not? I think so. His assertion about the nature of the traffic appears to be contradicted by Nigel West, who, in Venona, on page 120, presents an alternative explanation. He writes: “ . . . in 1959 the Swedish National Defence Radio Institute (Forsvarets Radioanstalt, FRA,) revealed that it had retained copies of a vast quantity of the Stockholm-Moscow traffic and negotiated with GCHQ to release its archive to the NSA via Cheltenham. This was the batch of intercepts codenamed HASP, and, bearing in mind that some of these texts had been encoded and signed by Petrov, there must have been a great temptation to confront him with them – if only to tax his memory by seeking clues to the missing, unrecovered groups.” West further explains that when the HASP material became available, ‘two 1945 VENONA intercepts from the Stockholm embassy, dated 16 July and 21 September, showed that Petrov, then codenamed SEAMAN, had been the personal cipher-clerk to two rezidents, first Mrs Yartseva, then Vasili F. Razin. However, their experience in Sweden had not prepared the Petrovs for the atmosphere of intrigue in Canberra.”
Thus West makes a very clear connection between traffic obtained locally in Sweden and the defection of Petrov and his wife in April 1954, and suggests, moreover, that HASP material was exclusively Stockholm-Moscow traffic. This is markedly in contrast to Wright’s representation. Yet West does not explain what the relationship was between the HASP and the VENONA material, how the former helped the GCHQ cryptanalysts, or where he derived his information. He refers to intercepts, but were these raw encrypted data, or partially decrypted texts – or both? The logic is very elusive, since the HASP messages are not separately identifiable, but it would appear that additional information enabled the cryptonym MORYAK (SEAMAN), as a key member of the Soviet embassy in Stockholm, to be identified as Petrov. And indeed, the source telegrams confirm Petrov’s statements from the memoir that he and his wife published in 1956.
The message of July 16 can be seen at: https://www.nsa.gov/Portals/70/documents/news-features/declassified-documents/venona/dated/1945/16jul_cipher_text_seaman.pdf, but the VENONA records of September 21 appear to contain no Moscow-Stockholm traffic. Nevertheless, the identity of SEAMAN can be confirmed from earlier traffic from Stockholm to Moscow, when Petrov was working in Moscow (see telegrams No. 797, of September 6, 1941, and No. 821, of April 30, 1942), before the Petrovs’ dramatic seven-month journey to Stockholm, via Siberia, South Africa, and Great Britain.
A significant distinction between the respective descriptions of HASP by Wright and West can thus be seen, with West, to support his cause, providing more tangible evidence of what the traffic contained. The account of another historian, Christopher Andrew, would appear to reinforce West’s description, although without actually mentioning HASP. On page 380 of Defend the Realm, Andrew writes: “Following requests during 1960, the Swedes supplied copies of wartime GRU telegrams exchanged between Moscow and the Stockholm residency, some of which were discovered to have employed the same one-time pads used in hitherto unbroken traffic with London. One hundred and seventy-eight GRU messages from the period March 1940 to April 1942 were successfully decrypted in whole or part.” Andrew’s message is explicit: these messages were not London-Stockholm traffic, but Stockholm-Moscow messages that the Swedes had apparently enjoyed some success in decrypting. His log of successful decryption applies to London-Moscow traffic, however, the suggestion being that both sets of traffic used the same one-time pads, and that no progress had been made by GCHQ on the London messages beforehand.
Moreover, what does that strange, anonymous notion behind ‘requests’ indicate? How did the ‘requestor’ learn about them? What was the crypto-analytical expertise of the Swedes, and had they previously shared experiences with GCHQ and NSA? The certain implication here is that the FRA had successfully deciphered some local GRU traffic, as West informed us. Yet it was not the messages themselves that were of relevance to GCHQ’s investigations, but a suggestion that the process of using stale one-time pads had been deployed, and that the revelations from these could be applied to traffic that the GCHQ possessed, but had been unable to break. This insight from Andrew (the source is the typically useless ‘Secret Service Archives’ from the authorised ‘historian’), and his immediately following comments, will turn out to be critical in working out what happened. It should also be noted that Andrew specifically contradicts Wright’s description of the essence of HASP, yet, with characteristic unscholarliness, includes Spycatcher in his bibliography.
Andrew’s failure to specify explicitly whether these one-time pads were the conventional set of random numbers created and printed by the KGB, or the alternative ‘reference-book’ mechanism used as a back-up system, is a critical oversight. I note also that this notion of ‘re-use’ suggests that deploying the same conventional pads across different intelligence stations was as much against the rules as was the ‘re-use’ over time of pads by a single pair of stations. Alternatively, it could mean that London-Moscow and Stockholm-Moscow both used the same reference-book in their emergency systems. In any case, this ‘re-use’ evidently occurred in 1940, well before the much publicized year of 1943 described in the VENONA histories as the time when the first infraction occurred. Andrew provides no guidance for his readers.
[ii] “GCHQ persuaded the Swedes to relinquish their neutrality, and pass the material over for analysis. The discovery of the Swedish HASP material was one of the main reasons for Arthur’s [Arthur Martin’s] return to D1. He was one of the few officers inside MI5 with direct experience of VENONA, having worked intimately with it during the Fuchs and Maclean investigations.
There were high hopes that HASP would transform VENONA by providing more intelligence about unknown cryptonyms and, just as important, by providing more groups for the codebook, which would, in turn, lead to further breaks in VENONA material already held.
The first point here is a reminder of Sweden’s neutrality – not just during World War II, but during the Cold War, when it was not a member of NATO. Like Portugal and Switzerland, Sweden had been abuzz with spies during World War II, and its proximity to the northern ports of German-occupied Poland and the Baltic States meant that Stockholm was well-positioned to supply information on German naval capabilities, repairs, etc. Hence the feverish wireless communications with Moscow. Moreover, that neutrality apparently endured, so that Sweden would not have been a natural sharer of decryption techniques with NATO members. Yet Sweden was not ‘neutral’ enough to be free of suspicions about Soviet intentions, and thus pursued its own program of trying to gather wireless intelligence.
In Venona, Nigel West relates how the Swedes collaborated with the more advanced, cryptanalytically speaking, Finns, who had provided the American with highly useful aids when they handed over the partially burned Petsamo codebooks that had been retrieved from the Soviet consulate in June 1941. And, no doubt, informal links were in place between the Swedes and the British, as Wright’s text suggests. West even indicates that the Finns managed to understand how the Soviets ‘built code-tables and relied on a very straightforward mathematical formula to encode emergency signals’, but it is not clear exactly how this happened, or whether the lessons learned applied to the GRU as well as to the NKVD.
Yet one overlooked event was John Tiltman’s acquisition of a GRU code-book retrieved from the body of a Soviet officer in1940. On Page 372 of his history of SIS, Keith Jeffery wrote: “In January 1940 Menzies asked Carr to find out if the Finnish authorities had ‘procured any Soviet cryptographic material which could be communicated to us’. Carr immediately replied in the affirmative and it was arranged that Colonel John Tiltman of GC&CS should travel out to Finland, where he was presented by Hallamaa with a Red Army code-book taken off a dead Russian officer and which ‘bore the marks of a bullet. GC&CS noted afterwards that it had been ‘of real assistance’ to their cryptographers.” It does not seem that this contribution, which predated the official recognition of the Petsamo code-book by five years, has ever been recognized in the few accounts of VENONA decipherment that exist.
Wright’s suggestion here, however, is that HASP was, in essence, different from traditional VENONA, although it is not immediately obvious in what manner. The implication is that HASP would share much with the VENONA traffic, such as the use of the same codebook (the reference by which otherwise meaningless sequences of numbers represented terms, functions, identities of persons, countries, institutions, etc., sometimes known as a nomenclator). The studies of VENONA tell us that the different functions of Soviet commercial organisations and intelligence (Amtorg, NKVD, GRU, Naval GRU and Foreign Ministry) used different code-books, and thus breakthroughs in one area did not mean that other successes naturally followed. For instance, all departments referred to the Germans as ‘KOLBASNIKI’ (’SAUSAGE-DEALERS’), but in the NKVD book, that word could have been represented as, say, ‘1146’, and in that of the GRU, ‘9452’.
This system was all independent of one-time pads for further encryption. Yet, if Andrew’s description is correct, Wright’s concluding sentence in this extract makes more sense. If the Swedes had managed to make inroads into the GRU codebook from the analysis of their local messages, that experience would transfer directly to the British study of GRU traffic. The emphasis on ‘VENONA material already held’ is telling. Wright is starting to backtrack from his original characterisation.
[iii] Moreover, since powerful new computers were becoming available, it made sense to reopen the whole program (I was never convinced that the effort should have been dropped in the 1950s), and the pace gradually increased, with vigorous encouragement by Arthur, through the early 1960s.
In fact, there were no great immediate discoveries in the HASP material which related to Britain. Most of the material consisted of routine reports from GRU offices of bomb damage in various parts of Britain, and estimates of British military capability. There were dozens of cryptonyms, some of whom were interesting, but long since dead. J. B. S. Haldane, for instance, who was working in the Admiralty’s submarine experimental station at Haslar, researching into deep diving techniques, was supplying details of the programs to the CPGB, who were passing it on to the GRU in London. Another spy identified in the traffic was the Honourable Owen Montagu, the son of Lord Swaythling (not to be confused with Euan Montagu, who organized the celebrated ‘Man Who Never Was’ deception operation during the war). He was a freelance journalist, and from the traffic it was clear that he was used by the Russians to collect political intelligence in the Labour Party, and to a lesser degree the CPGB.
Some of this is puzzling. Unfortunately, a detailed history of the evolutionary progress of the VENONA decrypts is not possible, based solely on the selection of documents released. As West writes in his Introduction: “Whereas the American policy appears to have provided a measure of protection to the living, being those suspected Soviet sources who were never positively identified or confronted with the allegations, their British partners seem to have adopted political embarrassment as their principal criterion for eliminating sensitive names. The only other deliberate excision in the declassified documents is the consistent removal throughout of all references to the first date of circulation. Each VENONA text is marked with the last, and therefore most recent, distribution, but it is impossible to determine precisely when the first break in a particular message was achieved, or to chart the subsequent program of the cryptographers.”
Overall, West’s statement is accurate, although some decrypts (such as those on BARON) do reveal a series of release dates, and others have had the issuance date deleted. Unfortunately, many of the critical items related to HASP, such as the discovery of the X Group, have no release dates at all, so it is impossible to determine how much of the messages had been decrypted before the contribution of the HASP codewords – and code-book. Wright’s seemingly authoritative view is that the project was suspended in the early 1950s, and then reactivated at the end of the decade, but the redacted (or concealed) data on the issuance of new decrypts does allow us to create only a very partial evolution of texts through time.
All this information described by Wright appeared as original VENONA material when described by West in Venona (pp 62-63), and it can clearly be traced by studying the on-line archive. So why does Wright revert to ‘the HASP material which related to Britain’? He appears to be going back to his initial position, that HASP consisted of traffic intercepted by the Swedes. That might have reinforced the idea that HASP was a motley set of messages that included local Stockholm-Moscow GRU/KGB traffic as well as interceptions of wireless messages between London and Moscow – and maybe more. Yet that scenario continues to look unlikely. And if these reports were ‘routine’, presumably familiar through VENONA messages already deciphered, why did Wright not say so?

Furthermore, he introduces Haldane and Montagu as if their appearance were no surprise, and not scandalous. Haldane’s cryptonym was INTELLECTUAL and Montague’s NOBILITY: when did Wright learn that? The appearance of these cryptonyms would not have been ‘routine’ if this was the first occurrence, and their identities were not known. In fact, it would have been a stunning discovery to learn that one of Britain’s most respected scientists was a named spy. The fact that they were dead was irrelevant – except when it came to GCHQ’s heightened protectiveness about references to hallowed public figures, and maybe to their survivors. Wright’s manner here is astonishingly casual.
It does not help that Nigel West (pp 75-81) presents the discoveries about Group X and Haldane as standard VENONA traffic without mentioning any contribution from HASP. He confidently identifies INTELLIGENTSIA as J. B. S. Haldane, and NOBILITY as the Honourable Ivor Montagu. After all, West’s understanding of HASP was that it concerned Stockholm-Moscow traffic: he writes that the arrival of HASP allowed the project to ‘be put back into gear’, but does not explain how that happened. West provides a lot of useful and fascinating information about Haldane’s background and activities, but (for example) sheds no light on how the decryption of the codeword INTELLECTUAL took place.
Christopher Andrew, however, is more explicit on this portion of the traffic, although he, too, still does not mention HASP, and the description of it as ‘new’ VENONA is misleading and unfortunate. “The main discovery from this new VENONA source was the existence of a wartime GRU agent network in Britain codenamed the ‘X Group’, which was active by, if not before, 1940. The identity of the leader of the Group, or at least its chief contact with the GRU London residency, codenamed INTELLIGENTSIA, was revealed in a decrypted telegram to Moscow on 25 July 1940 from his case officer as one of the CPGB’s wealthiest and most aristocratic members . . .” Thereafter, Andrew rather surprisingly goes on to identify INTELLIGENTSIA as Ivor Montagu, instead of ‘Montagu’s friend’, J. B. S. Haldane. In an endnote (p 926, No 81), Andrew states that ‘West misidentifies NOBILITY as Ivor Montagu and INTELLIGENTSIA as Haldane’, but provides no argument for this. Certainly the meaning of the two cryptonyms would appear to suit West’s interpretation better.
In 2012, Nigel West amplified his previous analysis in the Historical Dictionary of Signals Intelligence, where he added further detail: “. . . this unexpected windfall consisted of 390 partially deciphered messages, exchanged with Moscow between December 1940 and April 1446 [sic!]. The FRA had succeeded, as early as 1947, in reading a few messages, and between 1957 and 1959, some 53 texts were broken out. Information identifying individual Soviet spies had then been passed to the Allmänna Säkerhetstjänsten (General Security Service), which conducted investigations that effectively neutralized them without compromising the source.”
Apart from the vagueness of such terms as ‘broken out’ (does that mean complete decryption?), such level of detail is impressive, and authoritative-sounding, and West piled on the authenticity by naming eighty NKVD cryptonyms that provided ‘depth’ to the VENONA cryptanalytical process, including names that would carry import for the Washington and London operations, such as DORA, EDWARD, FROST, GROMOV, and LEAF. West then listed an even longer array of GRU codenames, nearly all unfamiliar to me. But he did explain that, in August 1942, Lennart Katz ‘a source run by a contact working under diplomatic cover named Scheptkov, was arrested’, and provided further leads. It sounds as if West had access to insider information (Venona provides an Acknowledgement to ‘Stefan Burgland and some others who prefer to remain anonymous’), and that those arrested may have been able to provide insights on the ciphers and codes used. Moscow, however, appeared not to have worked out what was going on, and how so many of its spies had been detected.
[iv] The extraordinary thing about the GRU traffic was the comparison with the KGB traffic four years later. The GRU officers in 1940 and 1941 were clearly of low caliber, demoralized and running around like headless chickens in the wake of Stalin’s purges of the 1930s. By 1945 they had given way to a new breed of professional Russian intelligence officers like Krotov. The entire agent-running procedure was clearly highly-skilled and pragmatic. Great care was being taken to protect agents for their long-term use. Where there seemed poor discipline in the GRU procedures, by 1945 the traffic showed that control was exerted from Moscow Center, and comparisons between KGB and Ambassadorial channels demonstrated quite clearly the importance the KGB had inside the Russian State. This, in a sense, was the most enduring legacy of the VENONA break – the glimpse it gave us of the vast KGB machine, with networks all across the West, ready for the Cold War as the West prepared for peace.”
This section is mostly irrelevant to the quest. It is difficult to discern what Wright is talking about when he does not provide samples of the messages. The KGB’s operation in London was (we have been told by several experts) suspended for nearly all of 1940, so the GRU was the only game in town. And these ‘headless chickens’ did manage to recruit Klaus Fuchs, and manage a ring of useful scientists, such as Haldane. What he may have been alluding to was the somewhat casual way that information was supplied in telegrams, but that would have been more a case of insufficiently well trained officers, cipher clerks, and wireless operators – which were evidently in short supply at the beginning of the war – rather than the quality of those who recruited and handled British agents. Kremer’s struggles with setting up the alternative wireless link may be an example of what Wright was thinking of.
Pp 238-239 “Lastly there was the VENONA material – by far the most reliable intelligence of all on past penetration of Western security. After Arthur [Martin] left I took over the VENONA program, and commissioned yet another full-scale review of the material to see if new leads could be gathered. This was to lead to the first D-3 generated case, ironically a French rather than a British one. The HASP GRU material, dating from 1940 and 1941, contained a lot of information about Soviet penetration of the various émigré and nationalist movements who made their headquarters in London during the first years of the war. The Russians, for instance, had a prime source in the heart of the Free Czechoslovakian Intelligence Service, which ran its own networks in German-occupied Eastern Europe via couriers. The Soviet source had the cryptonym Baron, and was probably the Czech politician Sedlecek [sic], who later played a prominent role in the Lucy Ring in Switzerland.”
Wright’s restricting of the ‘HASP GRU material’ to 1940 and 1941 is provocative, not solely because he now seems to be classifying HASP material as GRU messages collected locally. Is the temporal phrase ‘dating from 1940 and 1941’ merely adding chronology for the full scope of the material, or is it a qualifying phrase that subdefines a portion of it? The parenthesis, separated by commas, suggests to me the former, namely ‘the only GRU material that can properly be classified as HASP is that of 1940 and 1941’. Yet we have no way of knowing what GRU material had been attacked, and partially decrypted, before 1960, apart from various clues provided by the ‘experts’.
The rubric around the published VENONA messages is disappointingly vague. Yet there appears to be some discernible order behind the numbering scheme. In my analysis of the traffic between March 1940 and August 1941 (the last date in that year for which a message from London to Moscow has been published), I counted 137 L-to-M messages, with the first numbered (by the GRU) as No. 120, and the last as No. 2311. Yet a countback to zero seemed to occur at the beginning of each year. The last listed in December 1940 is No. 1424, while the first listed for 1941, on January 16, is No. 83. Thus one might assume that well over 4,000 messages were sent by the London station in those two years.
The Moscow to London traffic is sparser, with only 18 messages listed. The last calendar entry present for 1940 is from September 21, numbered as 482, so it would appear that Moscow was not so active sending messages to London, although the record would suggest that the combination of RSS (Radio Security Service) and GC&CS was picking up far fewer inbound messages, both in aggregate and proportionately, than it was outbound. But that could also be explained by a far smaller proportion of inbound messages being (partially) decrypted, or even a larger amount being for some reason concealed.
These numbers correspond closely with what Andrew has written (see above), where he refers to 178 messages between the period March 1940 and March 1942. Yet the autumn/winter of 1941/42 was clearly a period where activity of some sort (number of transmissions, number of interceptions, number of partial decryptions, number of released decryptions!) declined rapidly, and this is such a controversial aspect of the whole business that I shall return to it after completing my analysis of Wright’s text.
As for the remainder of this passage, the information, again, is not breathtaking, but Wright, alongside his rather laid-back commentary on Sedlacek [sic], does suggest by his comments that GCHQ had decrypted nothing on the Czechoslovak agent before the HASP project came along. Sedlacek [BARON] was a familiar figure in the VENONA traffic (see West, pp 67-69), and he played a dangerous game spying for the Swiss, the Czechs, the Russians – and the British, who later supplied him with a passport under the name of Simpson so that he could enter Switzerland and contribute to the Lucy Ring. Again, Andrew differs in his analysis of BARON, quoting (page 926, Note 82) an unnamed MI5 officer as saying, in 1997, that no serious attempts had been made to identify him. Why anyone would expect an MI5 (or MI6) officer to be open and straightforward about such a controversial figure as Sedlacek (if indeed that was who he was) is puzzling. Andrew attempts to reinforce his argument by noting that the NSA regards BARON as unidentified, but interest in these local European matters is unsurprisingly muted on that side of the Atlantic.
BARON indeed figures prominently in these messages: he was potentially very useful to Moscow as he was clearly passing on, in the run-up to Barbarossa, information about German troop movements in Czechoslovakia, Poland and Hungary, gained via his contacts around Prague who were transmitting information to him via Woldingham. I write ‘potentially’ because, of course, Stalin ignored all intelligence about the German invasion as ‘provocation’.
P 374-375 [i] “There had recently been a small breakthrough in the existing traffic which had given cause for hope. Geoffrey Sudbury was working on part of the HASP material which had never been broken out. Advanced computer analysis revealed that this particular traffic was not genuine VENONA. It did not appear to have been enciphered using a one-time pad, and from the nonrandom distribution of the groups, Sudbury hazarded a guess that it had been enciphered using some kind of directory.
This, again, is distressingly vague. By alluding to ‘HASP material that had never been broken out’, Wright again gives the impression that HASP was a collection of London-to-Moscow (or Moscow-to-London) communications. Why would Sudbury work on native Swedish transmissions? Presumably, ‘genuine VENONA’ to Wright was traffic that had become decipherable because the Soviets, under pressure, disastrously re-used one of their one-time pads. Distributing fresh pads was an enormous task in war-time, so the London-Moscow GRU link may have resorted to a different system whereby page-numbers and word-numbers in a shared book were used for encipherment schemes. Such a mechanism was essential for any transmission activity by clandestine agents, where the problems of distribution and security with one-time pads would have been insuperable. Leo Marks composed easily memorable verses for use in the field by SOE agents: the GRU used statistical almanacs for in-house use.
On the surface, Wright’s description of Sudbury’s analysis would appear, however, to be reinforced by the few accounts of GRU espionage that we have. A classical description of the use of one-time pads has the original cleartext (the passage in native language) immediately processed by a portion of the one-time pad, normally the next page, which would then be destroyed. In many accounts of the Soviet system (e.g. James Gannon’s Stealing Secrets, Telling Lies), that was the only method. Yet some accounts indicate that the GRU used a different process of encipherment. Benson’s in-house history of the NSA informs us that Igor Gouzenko described the method during his interview by Frank Rowlett in October 1945, when he revealed the back-up system of using a shared reference book in place of classical one-time pads. (Oddly, in his CIA report, Cecil Phillips, who assisted Nigel West in his researches, elides over this aspect of Gouzenko’s contribution.) In Appendix A to his 1949 book, Handbook for Spies, Alexander Foote (the Briton who was trained by SONIA as a wireless operator for the GRU in Switzerland) explains how a keyword of six letters, ‘changed at intervals by the Centre’ (and thus presumably communicated in later messages) was first used to translate the letters of the alphabet into a set of apparently meaningless numbers. Further manipulation transformed the text into five-figure groups – not yet a very secure encipherment.
Then came the ‘one-time’ aspect of the GRU’s process – but it was not through the use of a ‘pad’. Messages were then further processed by a function known as ‘closing’. Foote explained that, after the first stage of encipherment, he had to ‘close’ the message ‘by re-enciphering it against the selected portion of the “code book”’. (This ‘code-book, or ‘dictionary’ is a different entity from the ‘codebook’ that contained numeric representations of common terms.) This was a mechanism whereby a passage in a book owned by both parties was referred to by page and line number in order to identify a sequence of characters to be used to encipher a text one stage further. Max Clausen used a similar technique when enciphering for Richard Sorge, another GRU agent, in Japan. Foote said that he used ‘a Swiss book of trade statistics’: David Kahn writes that Clausen used the 1935 edition of the Statistiches Jahrbuch für das deutsche Reich. Thus, for the GRU, the one-time pad was not a miniature printed guide that could be easily destroyed, but an accessible but otherwise anonymous volume that could be used by both ends of the communication. (Christopher Andrew’s claim that the Stockholm residency and the London residency employed the same one-time pads is thus probably not true: they almost certainly used the same – or a similar – reference work, however.) Sudbury had indeed hit upon the truth, and a directory was at work. This is what must be meant by ‘not genuine VENONA’.
What should also be recorded on this topic is the claim that Richard V. Hall makes in his ineptly titled but engrossing study of Wright and the Spycatcher trial, A Spy’s Revenge, that Wright acted as a ghost writer on Handbook for Spies. Since Wright was still working at the Admiralty Research Station in 1949, and did not join MI5 until 1955, this claim should be viewed circumspectly. If true, Wright’s apparent unawareness, in 1970, of GRU enciphering techniques is even more inexcusable.
[ii] We began the search in the British Library, and eventually found a book of trade statistics from the 1930s which fitted.
At first glance, this represents an enormous leap of faith. From ‘some kind of directory’ to stumbling on a book of trade statistics, with the implication that many others had been tested and found wanting first? Can it really be believed? That that is how the process worked, and that cryptologists would stumble on the right book? They must surely have been able to exploit a message that described the volume to be used, or gained a tip from someone. Suddenly, Alexander Foote’s hint of a ‘Swiss book of trade statistics’ takes on new significance. Wright echoes Foote’s words almost completely. Foote had died in 1956 (somewhat mysteriously: I am sure that Moscow’s ‘Special Tasks’ team was after him), but was surely interviewed on these matters at length by MI5 and GCHQ before he died.
Thus the dominant reaction should be: why on earth were Sudbury and Wright not familiar with Foote’s publication? It seems quite possible that they arrived at this conclusion by other means – namely what the Petrovs told them, and how Vladimir’s overall cryptological skills and knowledge, and particularly Yevdokia’s experiences as a NKVD cipher-clerk in Stockholm, benefitted the FRA, and in turn helped GCHQ. Yevdokia had worked for the GRU in her first eighteen months with OGPU, so she may have had some insight into its coding techniques.
After their post-war assignment in Stockholm, Vladimir Petrov and his wife had arrived in Australia in 1951, and decided to defect in 1954. Nigel West writes that Evdokia ‘was debriefed by western intelligence personnel, among them MI5’s George Leggett, who travelled to Australia after the couple had been resettled on their chicken-farm . . .’ Yet what Evdokia told them has not been disclosed. Was she responsible for GRU coding and encipherment, as well as that of the NKVD/MGB/KGB? Almost certainly not, but if so, she might have been able to inform the Swedes of such items as the name of the code-book (dictionary) used, and they thus were able to make some progress on the texts they had stored before the British did anything. If she had no involvement with the GRU, she might have been able to indicate the type of research volume that was used, and repeated efforts by Sudbury on the few relevant books of trade statistics in the British Library must have eventually borne fruit. Wright’s claim becomes clearer. It looks, however, as if the Swedes kept their project to themselves until 1959, when, for some reason, an informal link must have been elevated to an official communication.
[iii] Overnight a huge chunk of HASP traffic was broken. The GRU traffic was similar to much that we had already broken. But there was one set of messages which was invaluable. The messages were sent from the GRU resident Simon Kremer to Moscow Center, and described his meetings with the GRU spy runner, Sonia, alias Ruth Kuzchinski [sic].
This is very dramatic – ‘overnight’, but, again, Wright dissembles and confuses. If the traffic was suddenly ‘broken’, he suggests that ‘HASP’ was in the hands of GCHQ already, but in a poor state of decryption. Now, HASP appears to mean ‘GRU traffic derived from both Stockholm and London’. But why next characterise it as ‘the GRU traffic’ – what else could it be? And what does ‘similar to’ mean? Were they the same messages, enciphered differently? Was there really nothing new in them worth recording? And his reference to ‘one set of messages’ is also ambiguous. He gives the impression that this was a new trove of London-Moscow traffic supplied by the Swedes, when we now know that that cannot be true.
Certainly, one meeting between Sonia and her handler is recorded in the VENONA transcripts, dated July 31, 1941. The full item appears as follows:
“From London to Moscow: No.2043, 31 July 1941
IRIS had meeting with SONIA on July 30. Sonia reported (15 groups unrecovered):
Salary for 7 months: 406
John: 195
?? from abroad: 116
Expenditure on apparatus (radio and microdots): 105
?? Expenditure: 55
She played [broadcast] on 26, 27, 28 and 29 July at 2400, 0100, 0200 hours . . . but did not receive you. BRION
(Comments by translator: IRIS probably a woman, IRIS means either the flower, or a kind of toffee. Unlikely choice for covername. JOHN probably Leon BUERTON [sic] BRION probably SHVETSOV, Assistant Military Attaché.)”
Yet the handler here is not Kremer: IRIS is probably Leo Aptekar, a GRU officer registered as a chauffeur at the Embassy. The annotation here about BRION is wrong: BRION has been confidently identified in the Vassiliev Notebooks as Colonel Sklyarov, for whom Kremer worked. Wright (and the VENONA website) identify Kremer as the rezident, i.e. senior GRU officer in London, but that does not appear to be the case. In Venona (1999), Nigel West described Kremer as being Sklyarov’s secretary, but in his 2014 Historical Dictionary of British Intelligence, West declares that the position was a cover for his ‘residency’, citing Krivitsky’s warning about him from 1940. Gary Kern (the biographer of Krivitsky) reflects, however, on the fact that others claim that Sklyarov was the boss. My analysis suggest that Sklyarov may have been brought in because Kremer was struggling, and Kremer then probably reported to Sklyarov after the latter arrived in October 1940. After all, Kremer turned out to be an unsuccessful cut-out for Fuchs, a role he would have hardly attempted had he been head-of-station. This is Pincher’s conclusion, too.

One of the irritating aspects of the Venona archive, as published, is that identification of codenames switches from page to page, and the identification of BRION is one such casualty, with the annotators not being able to make up their minds between Sklyarov and Shvetsov. Vladimir Lota, in his ‘Sekretny Front General’novo Shtaba’ (Moscow 2005), confirms that BRION was Sklyarov, and offers a photograph of the officer (see above). West selects one VENONA annotator’s analysis that the reporting officer was Shvetsov, but informs us that Shvetsov died in an air accident in 1942. (The source of this is not clear. The Petrovs record that the family of an unnamed London military attaché died in transit from Aberdeen to Stockholm in 1943, when the plane was shot down over Swedish territory by German aircraft, but suggest that the attaché himself was not on board. See Yuri and Evdokia Petrov’s Empire of Fear, p 165).
As for Kremer, Mike Rossiter, the author of a biography of Klaus Fuchs, writes that he returned to Moscow in 1941, while West indicates that he remained in London throughout the war. Thus it is quite possible that Kremer composed reports on Sklyarov’s behalf, although his role had hitherto been as a courier. It was he who met Fuchs in August 1941, and he was Fuchs’s courier until the latter found he could not work with him, whereupon Fuchs was handed over to Sonia in the late summer of 1942. Kremer was also handling members of the X Group, so it seems unlikely that, at the same time that Kremer was regularly meeting Fuchs, he would also be meeting Sonia frequently, and then writing up the reports for Moscow.
The VENONA London GRU Traffic archive informs us that Kremer [BARCh] ‘was appointed in 1937 and is thought to have left sometime in 1946. The covername BARCh occurs as a LONDON addressee and signatory between 3rd March 1940 and XXth October 1940, after which it is superseded by the covername BRION.’ (This analysis relies on the surviving VENONA traffic only, of course.) BRION first appears as a signatory or addressee on October 11, 1940. Thus the HASP traffic might provide evidence that Kremer was still active, as courier or signatory, or both, or, alternatively, the VENONA records might throw doubt on Wright’s claims about HASP. All three officers (Kremer, Sklyarov, Shvetsov) were active in London on June 7, 1941, as they are all cited as donating part of their salaries to the Soviet government.
The bottom line on Wright’s observations is that we are faced with another paradox. Apart from the fact that no trace of the ‘set of messages’ exists (why not, if they were solved overnight?), the association of Kremer with Sonia is very flimsy. The instance above is the sole surviving message in the VENONA archive that mentions SONIA. Wright’s account would imply the following: Apparently out of frustration with the fact that her transmissions received no response from Moscow, Sonia managed to contact the Embassy, and to meet her handler within a day or so. Sklyarov reported this event. At some stage afterwards, she was transferred to Kremer, who, apart from handling Fuchs, now had occasion to meet Sonia several times, and to make reports that he signed and sent himself. Yet the official archive informs us that Kremer stopped signing messages himself before Sonia even arrived in the United Kingdom.
What is also noteworthy is that Wright makes no comment about Sonia’s ability to escape radio detection-finding at this stage. If Sonia, as Kremer had recorded, had been transmitting for four successive nights, and had not been detected by RSS, one might have expected him, as a senior MI5 officer, to have reflected, at least, on her success in remaining undetected. He appears, at this stage, not to subscribe to the Chapman Pincher theory that Roger Hollis was able to interfere in the process; neither does he show any awareness that the proximity of Sonia’s home near Kidlington Airport might have masked her transmissions – which would admittedly have been a remarkable insight for that time. (It is probable that Sonia, and her husband, Len Beurton, adopted call-signs and preambles that made their traffic look, superficially, like British military signals, and that, should any remote direction-finding have taken place, the traffic’s origins would have been assumed to have been Kidlington airport itself.)
[iv] The Sonia connection had been dismissed throughout the 1960s as too tenuous to be relied upon. MI5 tended to believe the story that she came to Britain to escape Nazism and the war, and that she did not become active for Russian Intelligence until Klaus Fuchs volunteered his services in 1944.
Apart from an evasive non sequitur (the connection was held to be tenuous, but MI5 accepted that Sonia became active with Fuchs in 1944, a very solid interrelation), Wright enters dangerous territory here, with a vague and undated summary of what ‘MI5 tended to believe’. Fuchs, of course, volunteered his services in 1941, not 1944, and was in the United States throughout all of 1944. Yet Wright’s lapsus calami may reveal a deeper discomfort, in that he utterly misrepresents the pattern of events. According to the archives, after Alexander Foote had spilled the beans on Sonia’s activities in 1947, MI5 strongly suspected that Sonia had been working for the GRU in the UK. They were ready (or pretended to be so) to haul her in for questioning on the Fuchs case as early as February, 1950, before his trial was even over, apparently unaware that she had already fled the country! (The service probably connived at her speedy escape.) The Fuchs archive at Kew shows that in November 1950, and again in December, Fuchs, from prison, viewed photographs and recognized Sonia as his second contact. Wright was either hopelessly uninformed, or acting completely disingenuously.
[v] In particular GCHQ denied vehemently that Sonia could have been broadcasting her only radio messages from her home near Oxford during the period between 1941 and 1943.
But Kremer’s messages utterly destroyed the established beliefs. They showed that Sonia had indeed been sent to the Oxford area by Russian Intelligence, and that during 1941 she was already running a string of agents. The traffic even contained the details of the payments she was making to these agents, as well as the time and durations of her own radio broadcasts. I thought bitterly of the way this new information might have influenced Hollis’ interrogation had we had the material in 1969.
The statement attributed to GCHQ, if it indeed was made – and Wright provides no reference – needs parsing very carefully. We should bear in mind that no GCHQ spokesperson may have uttered these words, or that, if someone did state something approximating their meaning, Wright may have misremembered them. He provides no reference, no date, no name for the speaker.
First of all, Sonia’s home. She had, in fact at least four residences during this period, but, if we restrict her domiciles to those where she lived after she became active, probably in June 1941, we have Kidlington (from that June) and Summertown (from August 1942). Summertown was in Oxford, not near it. Thus a reference to ‘her home’ expresses lack of familiarity with the facts. ‘Only radio messages’ is perplexing. Does it mean ‘only those radio messages sent from her home?’, thus suggesting she could have sent messages from elsewhere? Maybe, but perhaps it was just a clumsy insertion by Wright. The omniscience that lies behind the denial, however, expresses a confidence that cannot be borne out by the facts.
It would have been less controversial for GCHQ simply to make the claim that no unidentifiable illicit broadcasts had been detected, and that Sonia must therefore have been inactive. But it did not. It introduced a level of specificity that undermined its case. It suggested that Sonia might have been broadcasting, but not from her home. If Sonia had been using her set, and followed the practices of the most astute SOE agents in Europe (who never transmitted from the same location twice – quite a considerable feat when porting a heavy apparatus, and re-setting up the antenna), she would likewise have moved around.
For GCHQ to be able to deny that Sonia had been able to broadcast would mean that it had 100% confidence that RSS had been able to detect all illicit traffic originating in the area, and that, furthermore, they knew the co-ordinates of Sonia’s residence at that time. Thus the following steps would have had to be taken:
- All illicit or suspicious wireless broadcasts had been detected by RSS;
- All those that could not have been accounted for were investigated;
- Successful triangulation (direction-finding) of all such signals had taken place to localise the source;
- Mobile location-finding units had been sent out to investigate all transgressions;
- Such units found that all the illicit stations were still broadcasting (on the same wave-length and with the identical callsign, presumably);
- All the offending transmitters were detected, and none was found to be Sonia’s.
Apart from the fact that transmissions from Kidlington were masked by proximity to the airport, and Sonia’s traffic concealed to resemble military messages, GCHQ’s assertion requires an impossible set of circumstances: that, if and when Sonia had broadcast, the location of the transmitter would have been known immediately, and the RSS would have been able to conclude that the signals could not be coming from Sonia’s residence. That was not possible. No country’s technology at that time allowed instant identification of the precise location of a transmission. Not even groundwave detection was reliable enough to ‘pin-point’ the source of a signal to the geography of a city, even. Reports and transcriptions of suspicious messages were mailed by Voluntary Interceptors to the RSS HQ at Arkley View, in Barnet! Sonia would have had to broadcast for over twenty-four hours in one session to be detected by a mobile unit operating at peak efficiency, supported by rapid decisions (which was never the case). GCHQ might have claimed to Wright that no illicit transmissions originated from the Oxford area, and therefore they could discount Sonia’s apparatus (if they knew she had one.) Yet, again, that would require RSS to have deployed radio direction-finding technology in order to locate the transmitter, and Sonia would surely have stopped broadcasting by then.
Thus GCHQ’s claim is logically null and void. If Sonia made only one transmission, from her home or anywhere else, she would never have been detected. If she made more than one, from the same location, she would (according to the RSS’s reported procedures) inevitably have been detected, interdicted, and prosecuted. And GCHQ’s claim that she made no transmissions is clearly false, as she did transmit from the semi-concealed site at Kidlington, which was apparently never picked up. (After the war, she broadcast from her next home, The Firs at Great Rollright, as Bob King of RSS has confirmed, but these events are strictly outside the scope of GCHQ’s claim here.)
Moreover, GCHQ (actually named Government Code & Cypher School, or GC&CS, during the war) was not responsible for intercepting illicit transmissions in 1941-1943: that was the responsibility of RSS, which reported to SIS. GCHQ took over RSS after the war. Institutional memory may be at fault.
Ironically, Wright then undermines the GCHQ statement as an unfounded ‘belief’, as if it were a vague hope rather than a matter of strict execution of policy. Thus, either Wright drills a large hole in the track-record of GCHQ’s inviolability, or his claims about Kremer’s reporting of ‘the times and durations’ of Sonia’s own broadcasts lack any substance – or a mixture of both, since, irrespective of Sonia, RSS may not have been perfect in its mission of pursuing all illicit broadcasts, as we know from its own files. And we also know from the VENONA transcripts that Sonia tried to contact Moscow on successive nights in July 1941, from Kidlington. Since RSS apparently did not detect any of these transmissions, GCHQ’s boasts of omniscience are flawed. Wright’s lack of expressed astonishment at the inefficiency of RSS is again a remarkable reaction. Moreover, why would Kremer report on such details of her transmissions, if she was successfully in touch with Moscow already? It was one thing to report her failure to get through, but these claims appear superfluous, even absurd.
How we treat this claim about Kremer’s reports on Sonia’s broadcasts depends very much on how reliable a witness one views Wright by now. As Denis Lenihan has pointed out to me, what Wright asserts contains so much fresh information that his claims should be taken seriously. On the other hand, I would say that the Kremer telegrams are simply too implausible to be considered as valuable evidence. That Sonia would have had a ‘string of agents’ by 1941, that they would need to be paid, that Kremer would consider it necessary to report to Moscow the details of recent successful transmissions she had made to Moscow, even the role of Kremer himself in meetings and handling Sonia, fail to pass the authenticity test with this particular analyst. West and Pincher apparently agree with me. West relegates the item to an endnote on page 70. Pincher ignores the whole matter: there is no mention of HASP in his Index to Treachery.
Lastly, we have to deal with the final claims. It would be very unlikely for a wireless message, sent to Moscow in 1941, to provide the information that Russian intelligence had specifically sent Sonia to the Oxford area, although that might be a reasonable conclusion for Wright to make. In addition, the claim that Sonia had rapidly acquired a ‘string’ of agents, and was seeking expenses for payments that she was making to these mercenaries, is very improbable. Where and how she acquired them is not stated, but any contact who might have been providing information to Sonia informally would have probably jumped with alarm if Sonia had suggested that he or she should be paid for such indiscretions. Even Sonia herself, in her memoir, stated that the informants she nurtured provided her with confidential information out of principle, not for payment.
Yet the most awkward part of this testimony is the declaration that MI5 did not have this evidence in 1969, when (so Wright claims) it might have helped with a more successful interrogation of Hollis. Wright explicitly indicates that the discovery occurred in 1970, or later. The critical discoveries that were made in the decryption of reference book-based random numbers for the process of ‘closing’ were revealed, however, in the 1960s. The VENONA records show that GCHQ tried to censor a series of the Moscow-Stockholm GRU traffic for the Version 5 release of the decrypts, and that the Swedes had to restore the excised passages in Version 6. I have studied all these messages: a few appear to have no relevance to British affairs at all, but several do specifically relate to the use of commonly owned books (knigi), and even identify the titles of the volumes. All these messages have an issue date in the mid-1960s.
We thus come to the conclusion that GCHQ and MI5 had four opportunities to learn of the use of a common book to be used by agents and clandestine embassy wireless when it was too dangerous to try to deploy conventional one-time pads: Gouzenko’s revelations in 1945; Foote’s disclosures in his memoir of 1949; the descriptions gained from questioning the Petrovs in 1954/55; and the experiences of the Swedish FRA when they handed over their decrypts in 1960. Practically all the final decryption work on GRU London-Moscow messages that was possible was completed during the 1960s, yet Wright tries to pass off the breakthrough by Sudbury, and the serendipity location of the directory in the British Library, as occurring in the 1970s.
[vi] Once this was known I felt more sure than ever that Elli did exist, and that he was run by Sonia from Oxford, and that the secret of his identity lay in her transmissions, which inexplicably had been lost all those years before. The only hope was to travel the world and search for any sign that her traffic had been taken elsewhere.
Over the four years from 1972 to 1976 I traveled 370,000 kilometers searching for new VENONA and Sonia’s transmissions. In France, SDECE told me they had no material, even though Marcel told me he was sure they had taken it. Presumably one of the Sapphire agents had long since destroyed it. In Germany they professed total ignorance. It was the same in Italy. Spain refused to entertain the request until we handed back Gibraltar. I spent months toiling around telegraph offices in Canada searching for traces of the telex links out there. But there was nothing. In Washington, extensive searches also drew a blank. It was heart-breaking to know that what I wanted had once existed, had once been filed and stored, but had somehow slipped through our fingers.”
This, again, is a very controversial statement. Wright refers to ‘Sonia’s transmissions, which inexplicably had been lost all those years before’. Yet mentions of Sonia’s transmissions have never surfaced until now: the HASP exercise concerned the GRU’s alluding to such messages. Wright has given no indication that any of Sonia’s transmissions had been intercepted, and he even cites GCHQ as saying she could not have operated her wireless set undetected. So, if they never existed, they never could have been lost. Moreover, the records of Kremer’s supposed transmission(s) have also been lost. Wright may have wished that he had them in time to interrogate Hollis, but he cannot even present them after 1970, when it was too late!
Thus an astounding aspect of Wright’s testimony is his apparent lack of curiosity in determining what happened to the missing messages. He does not investigate what policy might have led to these last sets of decrypted traffic to be buried or destroyed. Surely his named colleague Sudbury and his fellow-cryptologists must have kept some copies of these vital messages, or at least have some recall as to what happened to them? Yet Wright does not undertake a search domestically first, or invoke his associates’ help in establishing the truth, and hunting the transcripts down. He ventures no opinion on the fact of their possibly being destroyed, but simply looks overseas.
Maybe there was a glimpse of hope that other countries might provide further VENONA nuggets, but, since we now know that the Stockholm operation concerned local traffic only, the quest seems very futile. And why ‘telex offices’? Why Wright expected further evidence of Sonia’s transmissions to come to light in telegraph offices around the world is astonishing. In the United Kingdom, Sonia’s messages were illicit, and subject to surveillance, with Voluntary Interceptors dispersed around the country to pick up the ground-wave from suspicious transmissions. If, by any chance, her messages were noticed anywhere else, amongst all the other radio noise, it would have been remarkable for any institution, public or private, to have dwelled upon them long enough to transcribe and store them. And if GCHQ (RSS) was never able to detect them, why on earth would Wright expect some foreign entity to be able to do so?
In addition, the question was not whether ELLI existed or not, but who ELLI was, and how significant a player he or she had been, and when he or she had been active. If this is the piece that clinches the argument for the case that Hollis was ELLI, it stands on very unsolid ground. Exactly what the link was between Sonia’s ability to maintain a string of agents and the existence of ELLI is not made clear by Wright. Did Wright really believe that he would have been able successfully to confront Hollis with the transcripts of Sonia’s messages to Moscow, and challenge him on the grounds that he had been able to prevent superior officers in MI5, RSS and GCHQ from performing their jobs?
It all echoes the laborious claims made by Chapman Pincher that the only way that Sonia could have hoodwinked MI5, RSS and GCHQ so that they all turned a blind eye to her shenanigans was through the existence of an intriguer in the middle ranks of MI5 who was so devious that he could entice his colleagues to ignore the basic tenets of their mission. Presumably it was ELLI who, instead of warning Sonia that it might be dangerous for her to persist in her illicit transmissions from one single geographic location, somehow convinced RSS that its procedures could be put in abeyance, and the signals ignored, and, moreover, that corporate memory allowed this oversight to become enshrined in official statements of policy within GCHQ after the war.
The Remaining Questions
Two crucial questions arise out of all this analysis:
- What happened to the missing messages?
- Why did Wright mangle the story so much?
So much evidence conspires to inform us that what has been released to the archive of London-Moscow GRU traffic is only a small fraction of what was actually transmitted. The period of intensity is July 1940 to August 1941, followed by scattered fragments into early 1942, and a vast gulf until the end of the war, in 1945. The sequential telegram numbers tell us that less than 2% of the messages in 1940 and 1941 have been published. We have no idea how busy the communication link was during the next three years. We must therefore consider two separate sub-questions: i) given the ‘overnight breakthrough’ described by Wright, why were more messages in the 1940-1941 period not decrypted?, and ii) why was there a drought from the winter of 1941-1942 onwards?
The first sub-question cannot be answered by external analysis, as we do not know whether all messages were intercepted, which of these succumbed to even partial decryption, and which then remained classified because of issues of sensitivity or confidentiality. I do point out, however, that the official US VENONA website informs us that GCHQ did not hand over to the USA 159 of the GRU messages (i.e. close to the number I highlighted earlier) until 1996 – after the general disclosure of the VENONA project, indicating a high measure of discomfort about the disclosures (such as the Group X information).
What is also significant is that, having been passed decrypts from the Swedish authorities, GCHQ actually removed sections of the translated text before passing them on (in Version 5) to the Americans, with the result that the Swedes had to restore (in Version 6) the excisions GCHQ had made. Thus many messages in the VENONA archive include the puzzling rubric in their headings: “A more complete version of British Government-excised messages previously released in fifth VENONA release on 1 Oct 1996.” These revelations would seem to prove the case that the Swedes had made partial decryptions of their local GRU traffic, that they send these translations alongside the original messages, to GCHQ. It does not explain why GCHQ thought it was its business to edit them before passing them on to the NSA, especially if they also passed back their treatments to the Swedes at the same time. A close analysis of all the relevant changes in Version 5 and Version 6 would be desirable. As I have indicated earlier, many of them have to do with the disclosures about shared reference volumes.
The Drought of 1942-1944
The second sub-question lays itself open to deeper inspection, because of the availability of other sources. On the matter of the missing messages, we need to judge:
- Did they not exist?
- Did they exist, but were never intercepted?
- Were they intercepted, but never stored?
- Were they stored, but subsequently lost?
- Were they discovered, but not decrypted (even partially)?
- Were they decrypted, but then not released?
The first issue is especially fascinating, partly because of Alexander Foote’s experience (or, at least, how he reported it). In October 1941, the Germans were at the gates of Moscow, and the vast majority of Moscow’s government apparatus was moved to Kuibyshev (now Samara), over a thousand kilometres to the east. In his testimony to MI5 in 1947, Foote told his interviewers that, working out of Switzerland, he lost contact with his controllers in Moscow in the middle of October, and, a few days later, even cabled Brigitte (Sonia’s sister) in London to determine what had happened. He then claimed that contact was not restored until March 1942, when he resumed his broadcasts. (This is all in Handbook for Spies, as well.)
Yet the existence of this forced hiatus is belied on at least two fronts. The TICOM (Target Intelligence Committee) archive indicates that Foote reported regularly during those winter months. Moreover, his boss, Alexander Radó (DORA) was using either Foote or another operator to communicate regularly with Moscow, as his memoir Codename Dora describes, with frequent messages about German troop movements. Radó echoes Foote’s story about the interruption, but states that it was on October 29 that he sent a desperate message to Moscow Centre. Contact was resumed at the end of November or the beginning of December, and all dated messages from October (the texts of which appear in Radó’s book) were re-transmitted. A telling detail indicates that Foote indeed was the chief wireless operator at this time: a TICOM interception shows that he reported on the source LOUISE from Berlin on December 3, and a related message listed by Radó of December 9 similarly reported on LUISE’s intelligence from Berlin. It could well be that Foote’s claim about radio silence was inserted by his ghost-writer at MI5, Courtenay Young – but why?
Radó’s telegrams are confirmed by Lota, who transcribes several of Radó’s messages from this period, and even includes photographs of a few from 1942. A satisfying match can be made between a telegram received on November 27, 1941 (Lota’s Document No. 37, on page 353), and Radó’s original message created on October 27 (p 76 of Codename Dora), confirming the delay before ‘Moscow’ returned to the air, and, incidentally, discrediting Foote’s account. Thus one might have expected a similar interruption to have occurred in London. Ivan Maisky, the Soviet Ambassador, tells us otherwise, however. Molotov remained in Moscow, and informed Maisky by telegram on October 17th that ‘most of the government departments and the diplomatic corps’ had left for Kuibyshev. This date, and the fact of the almost total evacuation of the Soviet government, are confirmed by other memoirs, such as Tokaev’s and those of the Petrovs. Maisky does not tell exactly when communications were re-established, but hints it was after only a few days, and he was then able to resume full contact. Thus he would have been able to pass on to the GRU officers inside his embassy what was happening, and they would not have made futile attempts to contact their bosses. Maybe, after a month, however, the watchers got tired of waiting for something to happen, and dropped their guard?
Then there is the ‘government policy’ theory. In Defending the Realm (p 376), Christopher Andrew, following up his comments about British government approval of Soviet use on ‘set frequencies’ (see above), writes: ”These radio messages were initially intercepted and recorded in the hope that they could eventually be decrypted, but interception (save for that of GRU traffic, which continued until April 1942) ceased in August 1941 because of the need to concentrate resources on the production of ULTRA intelligence based on the decryption of Enigma and other high-grade enemy ciphers. Interception of Soviet traffic did not resume until June 1945.”
This must be partially true. Yet Andrew shows a remarkable disdain for the facts in his endnote to this section, where he adds: “Since the intermittent Soviet reuse of one-time pads, the basis of the VENONA breakthrough, did not begin until several months after the German invasion of the Soviet Union in June 1941, the messages intercepted and recorded up to August 1941 proved of little post-war value to GCHQ.” Au contraire, maestro! There was practically nothing that was useful that occurred after August 1941, as Andrew himself records a few pages later, when he describes the disclosure of Haldane and the X Group, from July 1940. Moreover, Andrew does not explain why interception of GRU traffic continued for so long, or what happened to the messages stored. The VENONA GRU files show only two messages from 1942, both fragments, from January 19 (London to Moscow) and April 25 (Moscow to London).
Whether resources had to deployed elsewhere is a dubious assertion, too. Much has been made of the famous Footnote supplied by Professor Hinsley, on page 199 of Volume 1 of British Intelligence in the Second World War, where he wrote that ‘all work on Russian codes and cyphers was stopped from 22 June 1941’, variously attributed to Churchill himself or the Y Board. The Foreign Office had promptly followed up the Y Board’s edict by forbidding MI5 to bug the Soviet Embassy, or to attempt to plant spies inside the premises, but was apparently more relaxed about the activities of MI6 and GC&CS, which nominally reported to the Foreign Office. While it may have taken a while for the policy statement to seep through, we should note that the edict said nothing about stopping the interception and storing of messages.
Robert Benson’s in-house history of the NSA (of which a key chapter is available on the Web) contains far more direct quotations from British authorities, such as Tiltman, Dill, Marychurch and Menzies, than can be found (as far as I know) from British histories. It reinforces the message that interception of Soviet traffic fairly rapidly tailed off towards the end of 1942, and that, during 1943 and 1944 any messages that had been stored were actually destroyed, to the later chagrin of intelligence officers. But that was what the alliance with the Soviet Union meant: a severe diminution in attempts to exploit Soviet intelligence, and that pattern was echoed in the USA. Since, at that time, no progress had been made on deciphering Russian traffic, it may have made little difference. One might also point out that, unless RSS intercepted all traffic, and inspected it, they would not know which was GRU and which was not, which makes Andrew’s already puzzling claim about the extension for GRU until April 1942 even more problematic, unless RSS knew that the secondary clandestine line was for GRU traffic only. Moreover, Andrew does not present Hinsley’s argument as a reason for the cessation.
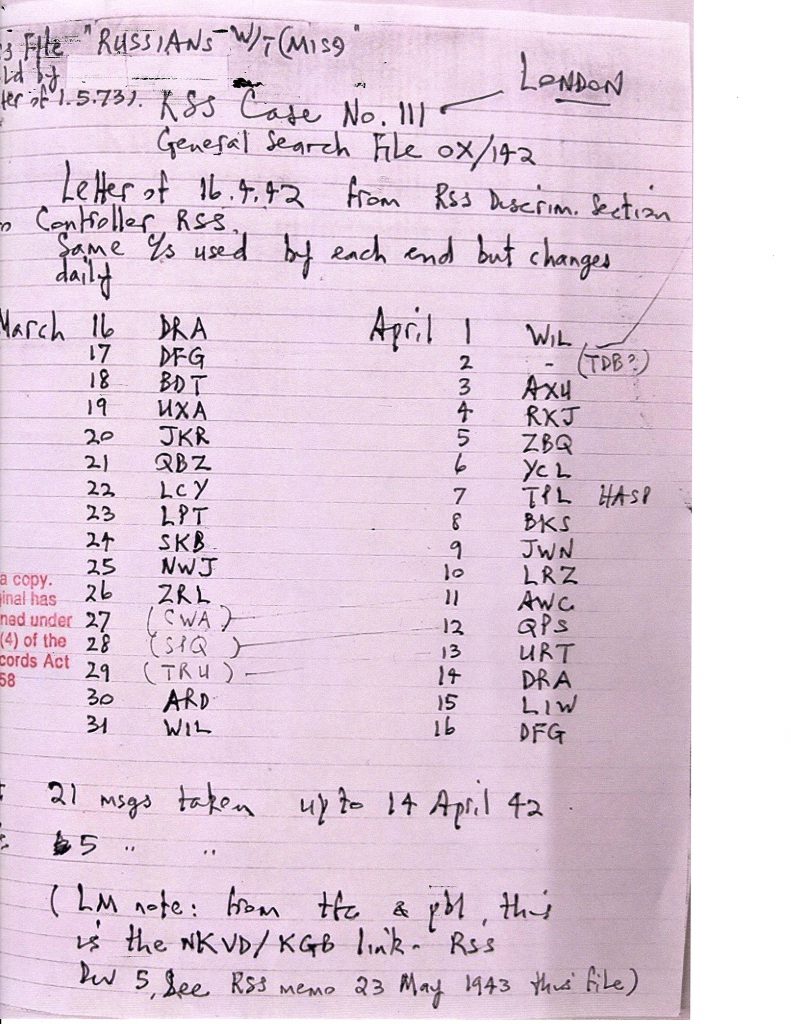
Certainly the Soviet Embassy was watched, and traffic was being monitored closely in March and April 1942. As I write, I have in front of me (see photograph above) the page from the RSS file HW 34/23, which shows a set of daily messages intercepted from March 16 to April 16, with callsigns, that changed each day, also listed. Very provocatively, the word ‘HASP’ has been written in opposite the April 7 entry, in what appears to be an annotation of May 1, 1973, and on the following page appears ‘from Maisky to Cadogan April 1942’, as if Maisky had perhaps had to explain himself to the Permanent Under-Secretary at the Foreign Office. (One cannot be certain that the annotation ‘HASP’ refers exclusively to the April 7 entry, or whether its serves as a general descriptor. If the latter, it would appear that, in 1973, the observer recognized this set of traffic, coming from the back-up GRU transmitter, as generic HASP material, but it does not explain how he or she reached that conclusion.) Other sheets suggest the surveillance went on into 1943. Yet all the evidence seems to point to the fact that, because of the signals being received from the Y Board and the Foreign Office, and the volumes of Nazi traffic to inspect, traffic from the clandestine line was either ignored, or simply piled up unused, and was discarded. Moreover, it was remarkably late for Wright (or whoever was the annotator) to be making, in 1973, a link between the HASP material of 1959 and the RSS files of 1943.
Nevertheless, a completely new project to monitor Soviet traffic was started at the beginning of 1943. After Commander Denniston had been replaced by Travis as the head of GC&CS in January 1942, he moved to London to set up a team that would begin to inspect and attempt to decipher Soviet diplomatic messages. This became known as the ISCOT project, after its key contributor Bernard Scott (né Schultz), and it led to the discovery of a rich set of ‘Comintern’ messages between the Soviet Union and its satellite guerrilla operations, after Stalin had supposedly closed down that organisation. Denniston was also involved in direction-finding the illicit traffic of 1942 to the Soviet Embassy. Thus, even if GRU/NKVD messages classified later as VENONA were ignored, it could hardly have been because of scarcity of resources. In addition, Andrew never explains why interception suddenly picked up successfully again in June 1945, and why RSS/GCHQ had no trouble finding the frequencies and call-signs used by the GRU.
A tantalising aspect of this whole investigation is the lack of overlap between published records of the GRU, and interceptions stored as part of the VENONA program. Verifiable records taken from Soviet archives are very thin on the ground, and we should be very wary of claims that are made of privileged access. Lota’s book (mentioned above) is a valuable source, containing multiple texts, and even photographs. It concentrates very much on military matters, especially concerning the movements of Nazi forces in the Soviet Union, and thus does not touch the early aspirations of the ENORMOZ (atomic weapons research) project. The familiar name of Sklyarov (BRION) appears quite frequently, but the first example of his telegrams is dated September 23, 1941 (Document No. 25). The VENONA sample of intercepted GRU messages from London (visible at https://www.wilsoncenter.org/sites/default/files/media/documents/article/Venona-London-GRU.pdf ) shows regular communications from BRION up to August 28, 1941, followed by a sprinkling of fragments up to March 1942, and then a long hiatus until 1945. Lota’s coverage thus overlaps in time, but I can see no messages that appear in both accounts.
Lastly, I must include the maybe very significant possibility that the rival channel set up in the London Embassy was not taken seriously enough. The official VENONA USA website offers (in ‘The Venona Story’) a very provocative paragraph, which runs as follows:
“Hundreds of GRU New York messages remain unsolved. The loss to history in the record of the GRU in Washington is particularly noticed. Of the several thousand Washington messages from 1941 to 1945, only about fifty were decrypted, in spite of the best efforts of the United States and the United Kingdom. Unlike the New York GRU messages, where translations concern espionage, these few Washington translations deal with routine military attaché matters (such as overt visits to U.S. defense factories). However, a separate Washington GRU cryptographic system, which was never read, presumably carried GRU espionage traffic.”
One might ask: ‘How did they know about this “separate Washington GRU cryptographic system’”?’ And what does ‘never read’ mean? That it was not intercepted? How did they know it was GRU if they never ‘read’ it? If it had been sent via cable, it would have been accessible, like all the other messages. Are the USA authorities referring to a clandestine wireless system, perhaps? And, if so, why did they not close it down? The reason these questions are relevant is that we have ample evidence that the GRU in London did attempt to set up a clandestine wireless system, and, after considerable teething problems, were apparently successful. (Vladimir Petrov confirms that such an arrangement happened in Stockholm, as well.) As I suggested earlier, it is possible that the RSS had worked out that the clandestine channel was for the GRU only. The intense USA focus of the VENONA website, and the various books that have been published in the US, mean that this project has not received the attention it deserves.
A closer inspection of the London-Moscow GRU traffic reveals the evolution of the project. The documents in this file are unfortunately not in chronological order, but a careful review suggests that the first reference is in a report dated July 17, 1940, from London to Moscow, where it is evident that a transmitter/receiver had been received in the diplomatic bag, but that the instructions for its assembly and deployment were deficient. London has to ask Moscow for the measurements for the aerial for MUSE’s apparatus. BARCh (Kremer) had decided to install the set in the lodgings of the military attaché, as he considered it was not safe in the Embassy, where the NKVD was ever-watchful. (“The only ones to fear are the NEIGBOURS’ people, who are in so many places here that it is hard to escape their notice.” This remark would tend to contradict the well-publicised notion that the NKVD staff had all been recalled to Moscow during 1940.) A few days later, however, it appears that Kremer has been ordered to change his mind, and install the radio-set in the Embassy, and is making rather feeble excuses about the lack of progress. On July 26, Kremer complains that the receiver works on 100 volts, which means it would be burned out by the 200-volt current in the embassy, and a transformer did not work. On August 13, they are back in the attaché’s house, where alternating current is available, and MUSE plans to try again, as a telegram of August 27shows. Kremer requests a schedule for the following months.
On August 30, 1940, reference is overtly made to the ‘London GRU emergency system’. The operator MUSE had been heard clearly, on schedule. Yet problems in communication begin to occur in September, and the Director begins to show impatience, reporting again on September 18 that MUSE’s message was not received in full. Maybe it was Kremer’s struggles that prompted the transfer of Sklyarov from New York. Kremer tries to get his act together. In a message of October 3, he remarks that Sklyarov’s arrival is impending. In the same message he reports that MUSE has had a successful communication with Moscow at last, and that she will be trying again on October 7. Yet it was not a proper two-way conversation. On October 10, 1940, one of the few messages from Moscow shows the Director informing Kremer of further problems receiving messages on the illicit line, with nothing received since September 18. The Director has to remind him of the correct wavelength, crystal, callsign, and time.
It takes Sklyarov himself to report on November 25 that MUSE is now ready to begin regular communication, and that is the last we hear of the link for a while. Presumably it worked satisfactorily. Yet a very significant message on July 31, 1941 indicates a hitch, and that MUSE has had to test communications again. Sklyarov asked Moscow how well they had received her. The reason that this could be so important is the fact that the only report on SONIA that appears in the extracts was transmitted the very same day, suggesting perhaps that the back-up system (for highly confidential espionage traffic) was not working. Similarly, the only message from this period referencing Klaus Fuchs is of a short time later, on August 10. It would seem, therefore, that Sklyarov had to resort to the diplomatic channel to pass on critical information. Nearly all of the messages in the intervening period (November 1940-July 1941) concern more routine military matters (as Wright reported), so the absence of any other information on SONIA, both beforehand and afterwards, could mean either that there were no reports, or that they were sent on the clandestine channel.
It was probably this traffic which excited RSS so much in the spring of 1942, when they tracked unauthorised wireless signals emanating daily from the Soviet Embassy, signals that displayed an unusual pattern of call signs. As I described above, Alexander Cadogan in the Foreign Office seems to have approached Ambassador Maisky about them, but may have received a brush-off. Yet why only one of these messages was annotated with ‘HASP’ is puzzling. It is as if the messages had been intercepted and stored, and one of them had been (partially) decrypted through the assistance of the HASP code-book. But, in that case, why only one? And where is it? Was it the missing message from Kremer claimed by Peter Wright to show SONIA’s recruitment of her nest of spies?
Moreover, one final crucial paradox remains, concerning the two rare messages I identified a few paragraphs earlier. In the 1940-1941 GRU traffic can be found only one message referring to SONIA (3/NBF/T1764 of July 31, 1941: transcribed above), and only one to Klaus Fuchs (3/PPDT/101 of August 10, 1941). The singularity is startling. In their book, Venona; Decoding Soviet Espionage in America, John Earl Haynes and Harvey Klehr offer (on p 439) a footnote on the Fuchs message, which describes Fuchs’s meeting with Kremer. Part of the note runs as follows: “This message is from a period antedating the Soviet duplication of one-time pads. Its decryption was made possible because the London GRU station in 1941 ran out of one-time pads and used its emergency back-up cipher system based on a standard statistical table to generate the additive key. British cryptanalysts working with the Venona Project recognized it as a nonstandard and vulnerable cipher and solved it, but not until well after Fuchs’s arrest.”
I found this analysis disappointingly vague. Apart from the unlikelihood of the GRU’s suddenly running out of one-time pads, the note did not indicate for how long the back-up system had to run, and how the problem of distributing new pads was resolved. I took a look at West again. On page 26, he writes: “The clerk [Gouzenko] also described the GRU’s emergency cipher system, and although this was considered at the time to have potential, it was never found to have been used apart from the 1940-41 London traffic, when the GRU apparently ran out of OTPs.” This was even more opaque. It threw the traffic for two whole years into the ‘back-up system’ bin, when a cursory inspection of the files indicates that the primary system was working well until Moscow and London started discussing the problem. Yet it rather wearily echoed the text that appears in The Venona Story, namely that ‘ . . . several messages deal with cipher matters — in 1940 to 1941, the London GRU used a so-called Emergency System, a variation of the basic VENONA cryptosystems. London GRU messages merit very close attention.’ Indeed.
I managed to contact Dr. Haynes by email, and asked him whether he could shed any light on the source of the footnote. He promptly responded, reminding me that two messages in the GRU trove from this period referred to the OTP problem, citing telegrams No. 410, of August 30, 1940, and No. 1036, of September 19, 1940. Yet Haynes and Klehr had cited 1941 in their note! These two messages were transmitted about a year before the phenomenon of the Fuchs and Sonia messages! How could an OTP problem remain unaddressed that long? Was the implication that the back-up system (using the reference book OTP on the diplomatic channel, as the new GRU wireless link was not yet working) was used for the next twelve months? How should this information be interpreted? I tactfully raised these questions with Dr. Haynes, but, even after conferring with Louis Benson, he has not been able to shed any light on the confusion over the expiration of the one-time pads, and the use of the back-up system, although Benson did offer the important information that he thought the British had ‘identified the standard statistical manual used to generate the additive keys’. But no date was given.
The sequence of events between April 1940 and March 1942, the period that encapsulates the most frequent of the London GRU traffic, is so confused that a proper assessment must be deferred for another time. The primary problem is that both London and Moscow refer, in messages presumably transmitted using the standard diplomatic channel, exploiting conventional one-time pads, of the imminent exhaustion of such tools. In that process, they ask or encourage the immediate use of the back-up system. Yet it is not clear that all successive messages use that back-up system, as later messages make the same appeal. It might be that the pads were in fact re-used as early as 1940. One enticing message (1036, of September 19, 1940) talks about ‘the pad used having been finally destroyed’, as if it should have been properly destroyed earlier, but was in desperation, perhaps, employed again, against all the rules.
In any case, a possible scenario could run as follows. Coincident with the GRU’s plan to move Sonia to Britain, to create a new espionage network, it decided to establish a clandestine wireless channel to handle her potential traffic. The task was entrusted to Kremer, but he struggled with getting the apparatus to work, and Sklyarov was transferred from New York to take charge. The conventional connection was used until November 1940, when the clandestine line was made to work, at about the time Sonia prepared to leave Switzerland. It was thereafter used successfully, until an interruption at the end of July 1941 caused Sklyarov to use the standard diplomatic channel for a critical message about Sonia – the only one to have survived in VENONA. RSS appears to have noticed messages on the clandestine link, but, if it did indeed intercept them and store them, no trace has survived. It is probable that no messages on that line were ever decrypted (apart from fragments at the end of 1941, and the two 1942 messages identified earlier). If other messages concerning Sonia were picked up and analysed from the standard link, GCHQ and MI5 must have decided to conceal them. (I have outlined this hypothesis to Dr. Haynes.)
Why did Wright mangle the story so much?
This close inspection of Wright’s account in Spycatcher shows a glorious muddle of misunderstood technology and implausible explanations. So why did he publish such an incoherent account of what happened? I present three alternative explanations:
- Wright simply did not understand what had been going on.
- Wright understood perfectly what had been going on, but wished to distort the facts.
- Wright had forgotten exactly what had been going on.
Number 1 is highly unlikely. He had been recruited as an expert with scientific training, and had showed knowledge of audio-electronic techniques to the extent that he uncovered Soviet bugs on embassy premises. He must have understood the principles of wireless communication, and the practical implications of intercepting both cable and wireless traffic. Number 2 does not make sense, as the mistakes that appear in his narrative tend to undermine any case he wanted to make about the identity of ELLI and the pointers towards SONIA. The sentence I cited above (in Cable or Wireless) is so manifestly absurd that it should immediately have alerted any knowledgeable critic to the fact that something was awry. If Wright had wanted to place a false trail, or was on a mission, he would have ensured that he appeared as a reliable expert on the main issues, but inserted subtle twists in the subordinate texts – in the manner in which Chapman Pincher operated. Wright definitely wanted to incriminate Hollis, but overall did not think he was distorting the truth, even if he was part of the ‘conspiracy’ to obfuscate what happened in the VENONA project. If he did embroider his account with the inclusion of an improbable and unverifiable message, he surely did not think it would be considered important, or that he would be found out.
Regrettably, one must conclude that, by the time Wright came to put his memoir together, he was approaching his dotage. Even though he was only seventy-one years old in 1987, his health was not good: he had high blood-pressure, shingles, and diabetes. In his account of the events, The Spycatcher Trial, Malcom Turnbull repeatedly draws attention to Wright’s failing health and faulty memory, pointing out that, as early as 1980 (when Wright was only sixty-four) he was too frail to travel from Australia to the United Kingdom by himself. Wright did not remember clearly how everything happened, how the intelligence services were organized, what the processes behind VENONA were, or exactly what HASP consisted of. His book was effectively ghost-written by Paul Greengrass, who clearly did not understand exactly what he was told by Wright, and, by the time it came for Wright to check the text, he was probably simply too impatient in wanting to see the book published, and consequently did not go over carefully everything that Greengrass had written. He was not concerned about the details: he wanted to get back at MI5 over its mistreatment of him on the pension business, he needed the royalties, and he was focused on getting the message on Hollis out.
I believe that it is entirely possible that, in his summoning up the telegram from Kremer that reported on Sonia’s network and payments, Wright was recalling the July 31, 1941 message that I reproduced in full above. It does mention agents and payments, but was sent not by Kremer, but by Sklyarov (BRION), mistakenly identified as Shvetsov in the annotations. We should not accept Wright’s account simply because, at one time, he had been an expert and a reliable witness. In addition, later reports suggest that there was an untrustworthy, almost devious, dimension to Wright’s behaviour. In his book on the trial, Malcom Turnbull expressed surprise at Wright’s ‘too uncritical worship’ of his mentor, Lord Rothschild. In his 2014 memoir, Dangerous to Know, Chapman Pincher asserted that Rothschild and his wife Tess loathed Wright, and he implied that Wright had exerted some kind of blackmail over the pair by threatening to include a chapter in Spycatcher that described Tess’s ‘long relationship with Anthony Blunt’.
As I indicated earlier, Chapman Pincher does not use his sometime accomplice Wright’s ‘evidence’ in his comprehensive presentation of the case against Hollis. Given that Pincher clutched at every straw he could find, and was always willing to present testimony from anonymous but ‘authoritative’ sources, this omission is somewhat startling. All Pincher states on Sonia’s recruitment of agents (beyond Fuchs and Norwood) runs as follows: “There is also new evidence that she and Len may have recruited and serviced a further fellow German communist – an atomic scientist working at the Clarendon Laboratory in Oxford, whose wife Sonia had met socially.” (p 198 of Treachery) Pincher also acknowledges that members of her family were informants for her, but dismisses Sonia’s claims about finding and recruiting ‘minor agents’ as possibly being a ‘GRU legendary cover’ (p 259). What this ‘new evidence’ consisted of is not explained, and the first statement has a very hypothetical ring about it. The conclusion, however, must be that Pincher did not trust Wright’s account of the breakthrough telegram.
Conclusions
Apart from the fact that ‘Spycatcher’ caught no spies, Wright was an unreliable witness. As D. Cameron Watt observed about the case: “A moderately careful reading of Wright’s book, let alone any checking of such statements he makes that can be checked, reveals, as most serious reviews of the book in the American press have shown, that Mr. Wright’s command of the facts, let alone his claims to universal knowledge, are such as to cast the gravest doubts on his credibility where his assertions cannot be cross-checked.” He completely misrepresented the structure of the VENONA project, and the material it used. He was likewise confused about the elements of the HASP program, and what the Swedes brought to the game. He magnified an illusory message, unlikely in its authorship, improbable in its content, and dubious in its objective, in order to promulgate a claim about Sonia that has no basis in any other facts, and to provide ammunition for a flimsy case that ELLI was Roger Hollis, the incrimination of whom he blatantly stated was his goal in publishing the book. In his muddled argument, he committed much damage to the other aspects of his case. At the time of the Spycatcher trial, even though he was only 71 years old, he was portrayed by Richard Hall and Malcolm Turnbull as an old, sick man, with a reputation for mendacity. He received the news of the outcome of the trial while in hospital.
The VENONA files, which should provide the archival evidence for his investigation, are in a mess. The USA website is very US-centric, it is scattered with spelling mistakes, chronologically misplaced items, contradictory and incorrect annotations about identities, misrepresentations of English place-names, and wayward references that could be cleaned up by recent scholarship. The British GRU traffic has been broken out, but it is out of sequence. An intense analysis of the pan-European communications could shed some strong light on a host of new relationships. A comprehensive index needs to be built, so that scholars could be more productive in bringing their expertise to bear.
HASP was a project that exploited GRU traffic between Stockholm and Moscow, which had been partially decrypted by the Swedes. It succeeded because of the policy that the GRU deployed, for the operations of clandestine and emergency services, and those of agents under their control, of using a common reference-book as a one-time pad. The Petrovs’ experience in Moscow and Stockholm contributed substantially to identifying the volume used. Thus dramatic improvements in decrypting certain London-Moscow traffic were made. Yet fresh work can be undertaken. The considerations of HASP, and other published material (e.g. Vassiliev), need to be incorporated into the British VENONA story (of which there is no ‘authorised’ publication at all, and nothing fresh since Nigel West’s book of 2009) and cross-referenced. An analysis of the excisions that the British Government is stated to have made between the Version 5 and Version 6 releases should be undertaken. In other words, it constitutes a major opportunity for GCHQ in the year that its authorised history appears. It needs a professional cryptanalyst to work on the source messages, and the evolution of the decipherment.
As I have written before, an authorised history of wartime and post-war interception services remains to be written. To begin with, the function crossed multiple organisations – not just all the intelligence services, but the War Office, the armed forces, the Post Office, even the Metropolitan Police. The Radio Security Service (RSS), of interest primarily to MI5, was never owned by the Security Service (despite Nigel West’s continued claims to the contrary), and was managed by a section of SIS from May 1941 until the end of the war, when GCHQ took control of it. Yet Keith Jeffery, in his authorised history of SIS, treated RSS (and GCHQ, which also reported to SIS during the war) as step-children. It will be interesting to see whether the coming history of GCHQ (Behind the Enigma, The Authorised History of Britain’s Secret Cyber Intelligence Agency, by John Ferris, due in November of this year), when covering the wartime years, treats RSS as an essential part of GC&CS (as it was then).
I believe that this bulletin provides an accurate account of the phenomenon of HASP, but a similar modern exercise needs to be performed against VENONA itself. After I post this report, I intend to draw the attention of the GCHQ Press Office to it. I ask all readers who would like to see some effort expended on clearing up this significant episode in British Intelligence History to contact the Press Office at pressoffice@gchq.gov.uk themselves, and thus reinforce my message.
(I regret that this research has been conducted without detailed access to the several files on VENONA at the National Archives, which have not been digitized. My previous superficial scans of the information did not indicate to me that the matters I have discussed were covered by the archival material at all. If any reader has found information in them that either clarifies, expands or confounds what I have written, please contact me. I also want to express my gratitude to Professor Glees, and to Denis Lenihan, for comments and suggestions they made concerning an earlier version of this article. Denis has continued to provide, right up to the completion of this report, very useful insights from the material he has analysed. Dr. Brian Austin has been a perennial outstanding adviser on wireless matters. I alone am responsible for the opinions expressed here, and any errors that may appear in the text.)
Major Sources:
Spycatcher, by Peter Wright
Venona, by Nigel West
GCHQ, by Richard Aldrich
The Code Breakers, by David Kahn
Stealing Secrets, Telling Lies, by James Gannon
Handbook for Spies, by Alexander Foote
The Code Book, by Simon Singh
Battle of Wits, by Stephen Budiansky
Stealing Secrets, Telling Lies, by James Gannon
Historical Dictionary of Signals Intelligence, by Nigel West
‘Sekretnyi Front General’nogo Shtaba’, by Vladimir Lota
Venona: Soviet Espionage and the American Response 1939-1957, ed. Robert Louis Benson & Michael Warner
Defend(ing) the Realm, by Christopher Andrew
The Haunted Wood, by Allan Weinstein & Alexander Vassiliev
Venona: Decoding Soviet Espionage in America, by John Earl Haynes & Harvey Klehr
The Venona Secrets: The Definitive Exposé of Soviet Espionage in America, by Herbert Romerstein & Eric Breindel
The Secrets of the Service, by Anthony Glees
The Secret History of MI6: 1909-1949, by Keith Jeffery
Empire of Fear, by Vladimir and Evdokia Petrov
Between Silk and Cyanide, by Leo Marks
Codes, Ciphers & Other Cryptic & Clandestine Communications, by Fred B. Wrixon
British Intelligence in the Second World War, Volume 1, by F. H. Hinsley and others
The Venona Story, by Robert L. Benson
MI6 and the Machinery of Spying, by Philip H. J. Davies
The Petrov Affair, by Robert Manne
A Spy’s Revenge, by Richard V. Hall
The Spycatcher Affair, by Malcom Turnbull
Treachery, by Chapman Pincher
Dangerous to Know, by Chapman Pincher
Peter Wright and the ‘Spycatcher’ Case, by D. Cameron Watt, in Political Quarterly, Volume 59, Issue 2, April 1988
The National Archives
https://www.wilsoncenter.org/sites/default/files/media/documents/article/Venona-London-GRU.pdf
https://nsarchive2.gwu.edu//NSAEBB/NSAEBB278/01.PDF
https://vault.fbi.gov/Venona/Venona%20Part%201%20of%201/view
https://digitalarchive.wilsoncenter.org/collection/86/vassiliev-notebooks
This month’s new Commonplace entries can be found here.

Interesting article. I share your frustration with the Spycatcher book though as there are many places in which details become vague and technically doubtful. It would be nice to know more about RAFTER (detecting low power radio signals transmitted by radio receivers). I can see how it was used to against the Soviet embassy having a presumably known receiver type in a fixed location but to use it to find illegals somewhere in London using an unknown receiver seems a bit of a stretch.
A couple of points though. The term “circuit” was frequently used to describe a radio link especially in the 40s/50s/60s but not so much now. Also a cable could have been sent by a telegraphic cable and via a radio link for part of its journey. A cable to a ship would be one example but also many countries had an internal telegraphic cable but then radio links to certain other countries. As late as the mid 80s most Albanian cables were still sent to outside countries via a HF (short wave) baudot code link every weekday afternoon. I know as I used to run home from school so I could receive that on a receiver bought from Currys and decoded it on a Commodore 64 computer !
Dear Ian,
Great to welcome you to coldspur! Thank you so much for the clarification. In fact, I had it at the back of my mind that some ‘cable’ messages might have been carried by wireless for part of their journey, but could never find verification of that phenomenon. (I shall emend my text, which is the beauty of Web posting.)
I was on less certain ground with ‘circuit’, but it just seemed logically not very sound to talk about a loose connection like wireless in that way. From what you say, terminology has tightened up a bit now.
But I think a lot of the VENONA-related writing is very sloppy.
Best wishes, Tony.
I have updated the article to reflect a very important addition, namely Keith Jeffery’s disclosure that John Tiltman acquired a GRU code-book from the Finns as early as February 1940. This item was recognised by GC&CS as providing very important assistance to the decipherment of VENONA traffic, although I have not yet been able to find any further account of it.
July 14, 2020
Tony regarding telex and HF you might be interested in this paper ..
https://cryptocellar.org/pubs/The_Biafran_Ciphers.pdf
Ian